Maritime security
Maritime security refers to the protection of vessels, both internally and externally .
The umbrella term covers issues related to national security, economic development, human security, and marine environment concerns .
Areas that are monitored and protected include oceans and territorial waters, regional seas, rivers, and ports. Maritime security strategies aim to track down and respond to crimes such as piracy, trafficking of people and illicit goods, illegal fishing, marine pollution, and armed robbery at sea.
For example, the European Union maritime security strategy (EUMSS) is a joint EU plan against all challenges from the ball-shaped maritime domain that may affect people, activities, or infrastructures in the EU. Some of the interests that are protected through the EUMSS include :
- Overall security and peace
- Rule of law and freedom of navigation
- External border control
- Maritime infrastructures: ports and harbors, coastal protection, underwater pipes and cables, offshore platforms, and scientific equipment
- Common natural resources and environmental health
- Climate change preparedness

Overview of Maritime Security Information Technologies & Operational Technologies
There are a countless of methods in which nautical security system is enforced. It’s imperative that in today’s 21st-century maritime environment, maritime security uses both information technologies (IT) and operation technologies (OT) onboard ships that are advanced and effective .
The development of digital and communications technologies has allowed the worlds of IT and OT to meet. As a consequence, nautical systems such as those below are created :
Vessel Integrated Navigation System
An integrated navigation system is one in which the information from two or more navigational aids is combined to provide an output that is superior to one of the component aids alone .
A Vessel Integrated Navigation System (VINS) ensures the safe operation of a vessel, with high accuracy and reliable position, speed, and attitude data .
Global Position System in Maritime
GPS has changed the means the populace navigates the globe—especially for marine operations .
It provides a fast and accurate way for mariners to navigate, measure speed, and determine location—ensuring guard and efficiency .
GPS is vital not only for at-sea navigation but also to provide governments and stakeholders with greater situational awareness of commercial vessels and their cargo .
Satellite Communications in Maritime security
High-speed satellite communication keeps ships connected with the prop up. When it comes to safety at sea, satellite communication provides ball-shaped strive through satellite and sublunar technologies .
When disaster strikes, such as a storm or collision, satellite communications provide seafarers with the ability to make distress calls and transmit priority messages over satellite communication networks such as Inmarsat .
Automatic Identification System
AIS or the automatic identification system is an automated tracking system that displays other vessels in the vicinity .
It uses transponders on ships to track and trace vessels —allowing the automatic electronic exchange of nautical information between ships and prop up installations .
Read A Complete Guide to Marine Traffic Tracking Technologies and AIS Data
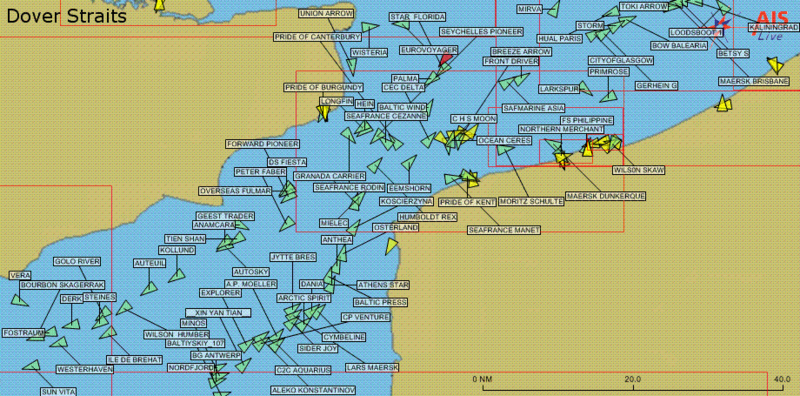 Above : A expose of nautical traffic provided by AIS in the English Channel. only vessels equipped with AIS are displayed, which excludes most fish boats, please craft, inland navigation, and vessels less than 300GT/
Above : A expose of nautical traffic provided by AIS in the English Channel. only vessels equipped with AIS are displayed, which excludes most fish boats, please craft, inland navigation, and vessels less than 300GT/
Radar system and electronic charts for maritime surveillance
Radar has retentive been how embark trailing has been done. It works by sending out a radio sign, which is reflected after hitting an object .
Although AIS vessel track has been the most significant development in navigational condom since the introduction of radar, it does not replace but supports radar systems for maritime security purposes .
The Electronic Chart Display and Information System (ECDIS) is a development that makes it easier for a ship’s crew to pinpoint locations and attain directions. With automatic path plan, monitor, and ETA computation—electronic charts are navigational information systems that interface with other equipment such as radar, GPS, and more .
Maritime security threats
Maritime security cyber-threats
The relatively holocene menace of cybersecurity at sea is one that the diligence must adapt to ensure safe seas .
Maritime cybersecurity refers to protecting the valuable data that a company holds, such as cargo information and employee details, which criminals can exploit. In the digital senesce, data auspices for IT systems, onboard ship hardware and sensors, a well as data leaks are critically significant .
Cybercriminals can also hack the electronic systems that control vessels. As the diligence becomes more automatize and efficient, this can result in dearly-won and severe ramifications .
Maritime cyber risk is a measure of the extent to which a technology asset could be threatened by a potential context or event, resulting in a shipping-related operational, base hit, or security bankruptcy as a consequence of information being corrupted, lost, or compromised .
Maritime security and piracy
Maritime security besides extends to an age-old problem in the high seas : piracy .
Known as the plundering, hijacking, or detention of a ship or boat—piracy has evolved over the centuries but remains a challenge .
typically the finish of plagiarism is to steal cargo and other valuable properties. Those who conduct piracy acts are called pirates, while the ships used are known as commandeer ships .
Although the term “ plagiarist ” may conjure up images of bearded men with eye patches, parrots, and wooden legs—pirate attacks are a significant terror to today ’ mho global ship lines .
What is anti-piracy?
contraceptive measures are a key component in the battle against maritime plagiarism. Anti-piracy measures are set up as a collection of actions or entities either at the ship, private security, or governmental level .
International Maritime Organization ( IMO ) regulations require ships to be able to send distress signals and warnings covertly in the case of a pirate attack .
To prevent plagiarist attacks, anti-piracy recommendations for the ship includes :
- Avoid discussing a ship’s route or cargo while in port
- Keep constant watch in areas prone to piracy
- Avoid bottlenecks in shipping lanes
- Search the ship before leaving port
In accession to crew ’ randomness precautions, regularly deployed anti-piracy missions aim to safeguard maritime trade and suppress plagiarism. Since 2008, the indian Navy has routinely been deployed for anti-piracy missions in the Gulf of Aden alongside other navies of the earth .
Anti-piracy missions aim to safeguard maritime trade and curb piracy in the region .

Maritime security to monitor maritime piracy
contemporary nautical piracy peaked in 2010, with 445 reported incidents —especially on trade routes between Europe, Africa, and Asia .
Usually, it is often the crew and pirates themselves who pay most dearly for maritime crime. In Somali waters in 2011, at least 149 crew members were held hostage, and over 100 pirates were killed—primarily by naval forces such as armed guards .
This kind of protective covering is a critical partially of nautical security to monitor nautical plagiarism, with armed guards playing a cardinal function in protecting merchant ships .
Security recommendations provided to vessels include reviewing ship security measures, ensuring AIS is transmitting at all times and monitoring radio channels .
Maritime piracy hot-spots
Piracy blistering spots of nowadays include areas of high traffic and ships carrying valuable cargo. Let ’ s look at some examples :
1. Gulf of Guinea
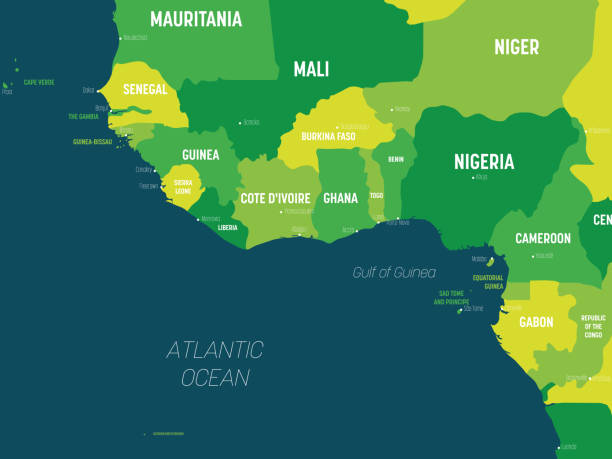
With its 11 countries, eight of which have proven anoint reserves and five of which are major fuel producers— the Gulf of Guinea was labeled the world’s most dangerous maritime zone in 2020 .
The IMB ’ s Piracy Reporting Centre recorded 84 attempted and successful attacks in 2020, up from the 64 in 2019. Most assaults targeted the crew to kidnap them for a ransom. nowhere on Earth do pirates strike more than the Gulf of Guinea .
2. Arabian Sea & Gulf of Aden
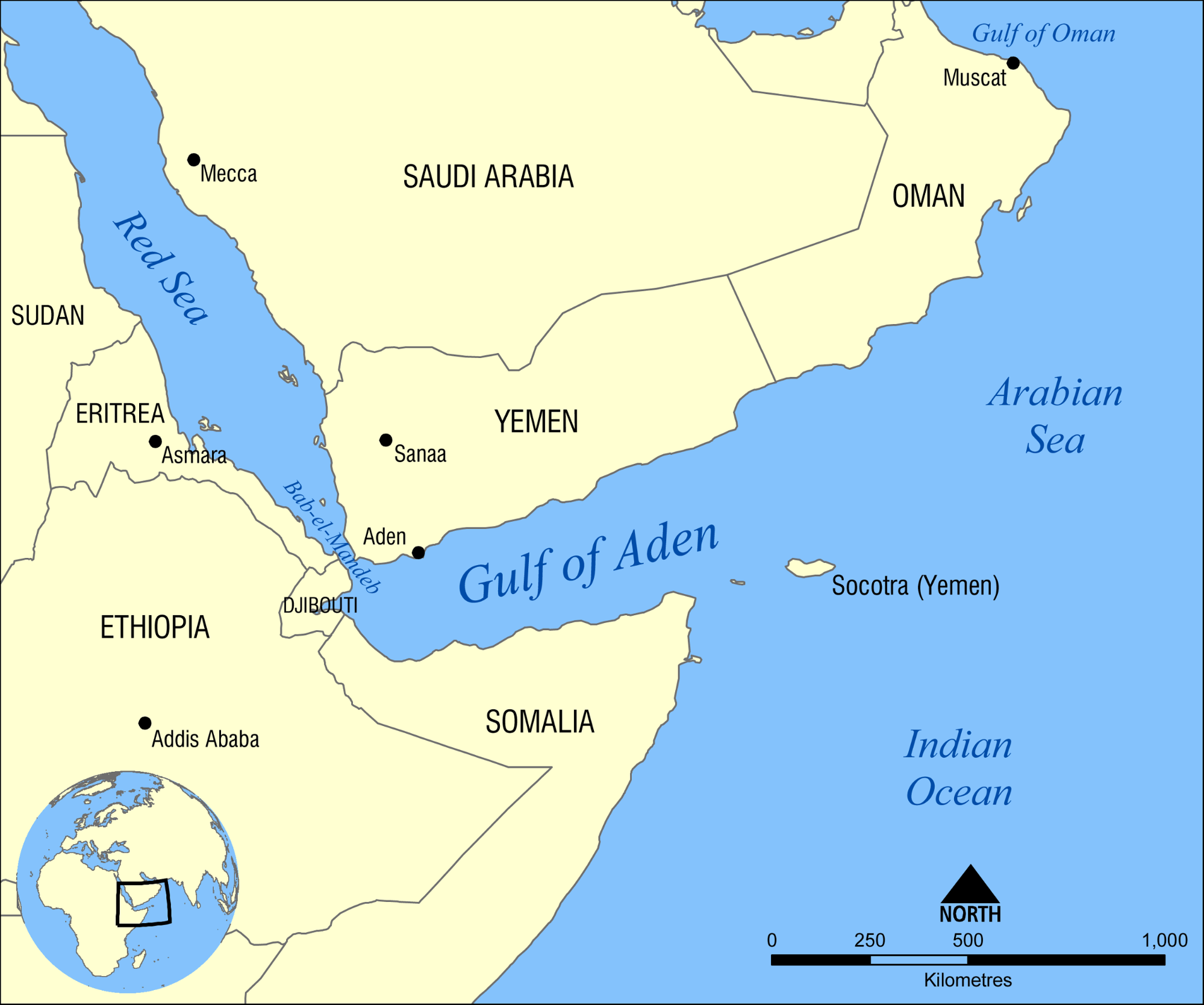
Piracy in the Arabian Sea, Gulf of Aden, and the Indian Ocean rose from 20 in 2006 to 219 in 2010. The US MARAD issued an advisory on 14 December 2020 concerning vessels operating in these areas, warning that piracy remains a risk for commercial vessels .
Organized piracy in the Gulf of Aden, the southerly submission luff to the Suez Canal, has become so frequent that the sphere has become known as “ Pirate Alley ”. This body of water system, already the most dangerous in the worldly concern for piracy, has grown increasingly treacherous as kidnappings, extortion, and hijackings have grown over the years .
3. Persian Gulf
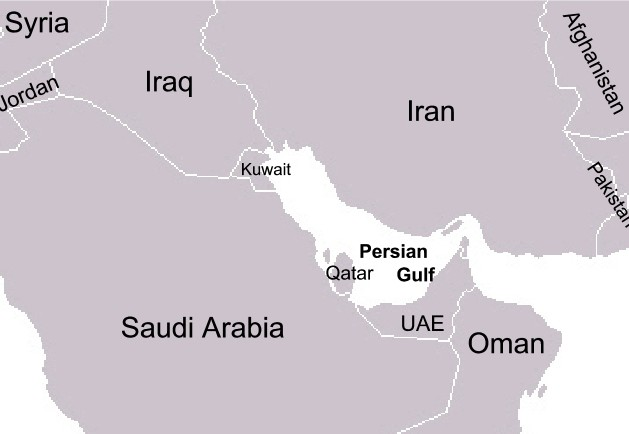
For decades, the alleged “ pirate-kingdoms ” of the Persian Gulf ’ s southerly coast ( present- day Qatar, UAE, and Bahrain ) have preyed on ships at sea .
plagiarism in the Persian Gulf was common from the late eighteenth hundred to the mid nineteenth century. It was alleviated in 1820 with the sign of the General Maritime Treaty, followed by the Treaty of Maritime Peace in Perpetuity in 1863. Today, piracy throughout the middle east region is considered a threat to the regional economy, and the global economy .
4. South China Sea
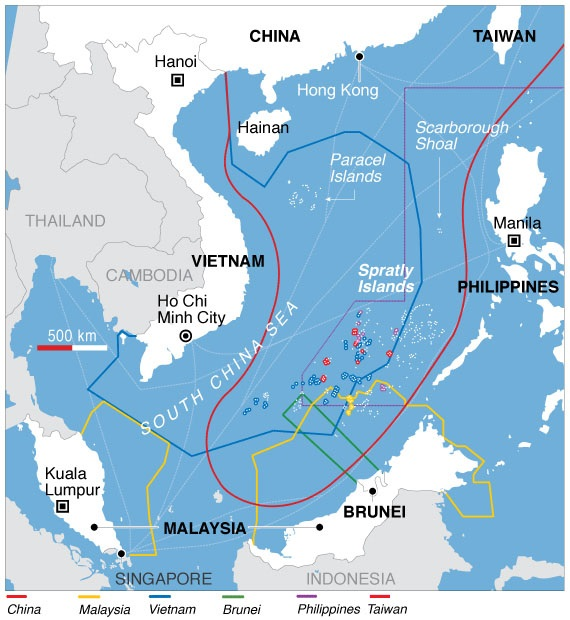
Piracy in Asia has increased to the highest level in five years due to ongoing territorial disputes in the South China Sea .
In 2014, the UN declared the South China Sea waters to be the most parlous in the earth. Stretching from Malaysia ’ s westernmost corner to the tap of Indonesia ’ s Bintan Island, the Malacca and Singapore straits serve as the world ’ randomness transportation superhighways .
between 70 % and 80 % of all the oil imported by China and Japan traverse these waterways—offering rich pickings for pirates. Well-armed and organized groups focus their efforts on the anoint tankers in this area, where the district is huge, law enforcement is stretched, and likely profits are huge .
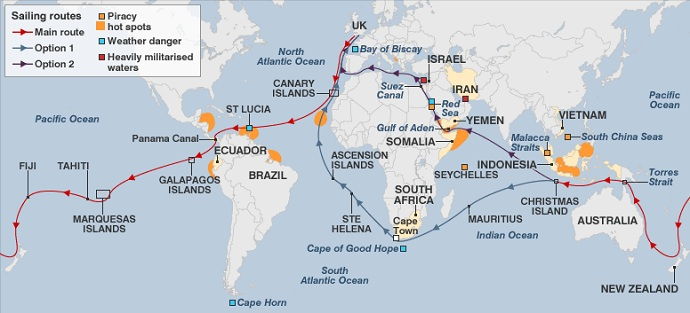 Hot spots and typical sail routes ( source : Maritime Connector )
Hot spots and typical sail routes ( source : Maritime Connector )
Illegal fishing
What is illegal fishing?
Illegal fishing refers to fishing carried out by overseas vessels with no authorization in waters under the control of the state or which breach rules and regulations. Fishing laws include acknowledging fish times and fish harvest in marine or water-protected areas .
west african coastal states lose up to $ 1.5 billion a year as a result of illegal fish .
Although maritime security strategies focus on the issues of human traffic, migrant smuggle, and piracy—illegal fishing is a growing problem that hits countries and ecosystems difficult .
An integrated approach to maritime security addresses the problems associated with the fisheries sector due to illegal fishing .
There are a battalion of types of illegal fish, including :
- Bottom trawling
- Bycatch
- Overfishing
- Ghost fishing
- Cyanide fishing
Illegal marine pollution
What is illegal marine pollution?
With growing environmental awareness, marine befoulment is much in the headlines and recognized as a crime that is worse than ever before .
Illegal marine pollution is polluting the sea through the illegal emission or discharge of substances such as pollutants .
A global mathematical process led by INTERPOL in 2019 identify thousands of illegal activities behind severe marine pollution. Many national laws, and international agreements now forbid the dumping of harmful materials into the ocean, but enforcing this is challenging.
Read more: A Man Quotes Maritime Law To Avoid Ticket
Marine contamination includes :
- Plastic pollution
- Oil seepage
- Sewage
- Industrial waste
- Agricultural and aquaculture runoff
 The Exxon Valdez petroleum spill : the oil tanker ran aground on a reef in 1989. Decades late, the alaskan environment is still feeling the effects. ( beginning : RGB Ventures/SuperStock/Alamy Stock Photo )
The Exxon Valdez petroleum spill : the oil tanker ran aground on a reef in 1989. Decades late, the alaskan environment is still feeling the effects. ( beginning : RGB Ventures/SuperStock/Alamy Stock Photo )
Custom infringements
In addition to the nautical security issues already discussed, crimes such as customs infringements and marine smuggle are besides areas of refer .
As borders become more capable and more people can travel to and from countries, issues related to the motion of material across borders have created a challenge for inspectors creditworthy for keeping bootleg out of the nation .
Custom infringements can include undeclared cash onboard subject to confiscation and fines of at least double the amount. To help with the screen process, customs departments use novel methods such as outback video inspection to locate an object even if it is hidden .
 Four seized bales comprised of 200 pounds of cocaine with estimated wholesale value of $ 3 million dollars lay aboard the Coast Guard Cutter Margaret Norvell ( WPC-1105 ) Jan. 30, 2019, following the interdict of a drug smuggling go-fast off the coast of Arecibo, Puerto Rico Jan. 29, 2019 .
Four seized bales comprised of 200 pounds of cocaine with estimated wholesale value of $ 3 million dollars lay aboard the Coast Guard Cutter Margaret Norvell ( WPC-1105 ) Jan. 30, 2019, following the interdict of a drug smuggling go-fast off the coast of Arecibo, Puerto Rico Jan. 29, 2019 .
Marine smuggling
When it comes to smuggling, the trafficking of drugs and people remains a growing concern .
While the maritime industry continually improves its anti-narcotics operations, traffickers are increasingly finding novel ways of smuggling drugs—such as inside vessel piping systems for an integral voyage .
The 2015 refugee crisis brought the universe ’ mho attention to human smuggling—a profitable clientele for criminal networks, smugglers use ocean routes to facilitate illegal migration .
Human smuggling is long associated with serious human rights violations and deaths, particularly when it occurs at sea. The loss of refugees ’ lives at the hands of smugglers in the Mediterranean Sea is a austere reminder of the want to tackle human smuggling—especially since networks are close linked to early forms of organized crime such as terrorism, human traffic, and money wash .
It’s important to keep in mind here that there is a significant moral element to consider when focusing on people smuggling and refugees fleeing for their lives. With much of the holocene public converse on immigration to Europe and refugees being forced to flee conditions of war and poverty—human smuggling exploits vulnerable people in need .
This study argues that human smuggling is morally permissible under some conditions, even if it is illegal. Human trafficking, by contrast, is immoral and should be illegal (Aloyo & Cusumano, 2018) .
 For refugees, smuggling is often the only option of scat. Some say more and quicker resettlement options for vulnerable people are needed as an alternate to crossing treacherous waters at the hands of smugglers .
For refugees, smuggling is often the only option of scat. Some say more and quicker resettlement options for vulnerable people are needed as an alternate to crossing treacherous waters at the hands of smugglers .
Coast guard and surveillance activities
Policing the high seas involves security support from those onshore. Coast guards are a maritime security organization specific to a country .
The condition encompasses a across-the-board range of responsibilities, ranging from being a heavily armed military force with security and customs duties to being a volunteer constitution responsible for search and rescue without law enforcement authority .
A distinctive coast guard ’ south duties are discrete to those of the navy ( a military service ) and the passage police ( a police enforcement agency ) .
Mitigating Maritime Security
Maritime Cyber Risk Management
As mentioned, the digital senesce brings digital risks to maritime security. To manage these cyber risks, it ’ randomness substantive to understand the tied of risk we are faced with .
Maritime cyber risk refer to a measure of the extent to which a technology asset could be threatened by a potential event or circumstance, resulting in operational, safety, or security failures as a consequence of information or systems being lost, corrupted, or compromised .
Cyber risk management is the process of identifying, analyzing, and assessing, and communicating a cyber risk .
then, accepting, avoiding, transferring, or mitigating it to an satisfactory level—taking into account the costs and benefits of actions taken to stakeholders .
The IMO has issued guidance on maritime cyber risk management to safeguard ship from stream and emerging cyber threats and vulnerabilities .
Safety Management System
On a embark, a safety management system or SMS is a systematic approach to managing safety. It ensures the condom of vessels and the people on board by following established policies, practices, and procedures .
All domestic commercial vessels must have a safety management system. This system demonstrates and documents how the vessel meets the mandatary general guard duties—which apply to everyone working on, traveling on, designing, build, or servicing the vessel .
A safety management arrangement is not barely a document though, it must be put into practice and be effective .
Maritime Transport Security Act
In the wake of the September 11, 2001 terrorist attacks, the US Congress passed the Maritime Transportation Security Act ( MTSA ) of 2002—directing the US Department of Transportation to develop security measures for domestic maritime facilities and vessels that call there .
This Act establishes a scheme to safeguard against unlawful interference with maritime transport or offshore facilities. It is a meaning piece of legislation that reinforces the national and global importance of security for the nautical transportation system system .
A systematic approach to maritime surveillance
Taking a systematic approach to ensuring safer seas can provide us with greater situational awareness through data sharing and coordination between unlike areas .
Emerging methods of administration such as the european Commission ’ sulfur Integrated Maritime Policy promotes such a cross-sectoral approach .
It seeks to provide a more coherent approach to maritime issues to identify and explore synergies between all EU policies relating to the oceans, seas, coastal regions, and maritime sectors—namely the nautical ecstasy, environmental, research, fishers, energy, industry, and regional policies .
Systematic approaches take account of the interconnectedness of industries and human activities centered on the sea—saving time and money while moving the world towards a more structured and systematic collaboration .
Leveraging geospatial data to build solutions for maritime security
maritime conditions can change in an instant. With geospatial data and insights derived from geospatial analysis, you can gain near-real-time situational awareness .
Geospatial data such as satellite imagination, weather data, and AIS data allows you to build solutions that integrate these data types and solve security challenges .
For model, satellite imagination from the Sentinel-1 satellite configuration provides the bigger picture over an area of pastime. Ship signal detection algorithm then accurately identify vessels visible within the satellite imagination .
This enables you to isolate ships of a certain size and validate their respective locations—in turn, monitor and understand vessel activity anywhere in the world with just the click of a button .
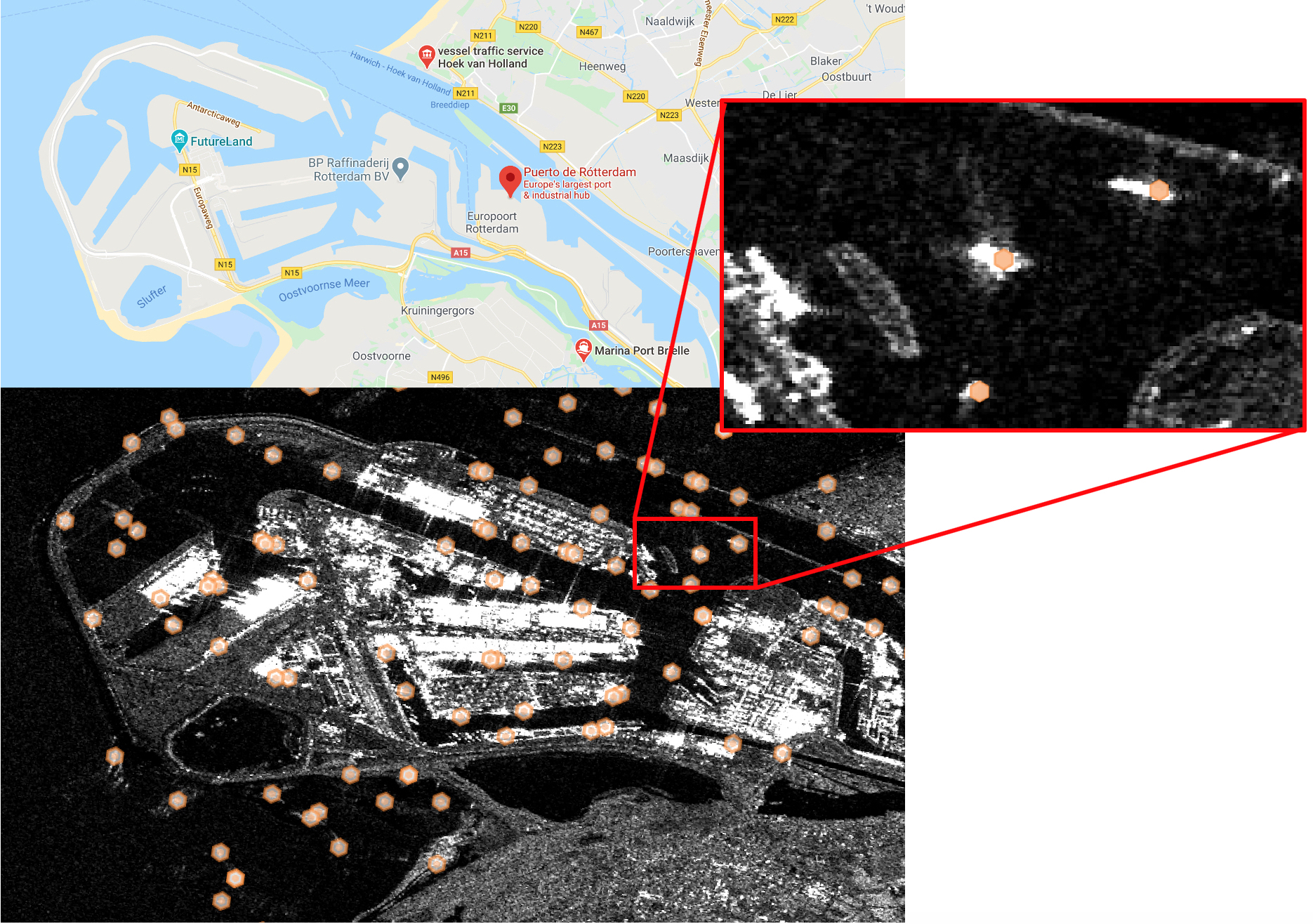 Above : A larboard management use case in the port of Rotterdam, Netherlands, the largest seaport in Europe, using Sentinel-1 radar data and a transport detection march block by osir.io .
Above : A larboard management use case in the port of Rotterdam, Netherlands, the largest seaport in Europe, using Sentinel-1 radar data and a transport detection march block by osir.io .
Port Security
A part of maritime security
The term port security is a separate of a broader definition concerning maritime security .
It refers to the security and law enforcement measures used to safeguard a shipping port from unlawful activities such as terrorism. Port security besides concerns the measures in place that ensure treaties entered into with early countries are enforced appropriately .
angstrom well as this, larboard security is a character of nautical security and focuses on the security of marine commercial areas, beaches, and coastlines .
Port security system comes under the horizon of the IMIO and the International Ship and Port Security Code introduced in 2002 as depart of the Safety of Life At Sea ( SOLAS ) convention. In addition to these organizations, many port security measures are incorporated from the UN ’ s own marine security enforcement agenda .
 source : BMT Press Office
source : BMT Press Office
Busy areas spread over a large area are a vulnerable target
Ports are busy areas and spread over a very boastfully sphere of space. Because of this, certain areas of ports can be inaccessible for patrols at all times—leading to cargo larceny and early crimes .
Port security is vital because marine transport, especially cargo transportation, is a thriving industry that requires diligent monitoring and inspection of transferred cargo .
Security risks related to ports normally focus on either the physical security of the port itself, or security risks within the nautical supply chain .
Port security includes the protection and inspection of cargo moving through ports through security guards, video surveillance, alarm systems, and more .
Threats
1. Theft To ensure that cargo larceny does not take place, physical port security risk management practices are put into target. This includes the employment of a security director and crisis leadership, and physical barriers such as CCTV cameras and adequate light at the port .
2. Sabotage Vessels calling at ports are susceptible to acts of sabotage. If maritime sabotage does occur, this can have unplayful effects on commercial transport and nautical transportation networks. sabotage attacks and terrorism against ship, ports, and terminals aim to threaten vessel missions and the seas’ safety .
In 2019, amid rising tensions between the US and Iran, sabotage attacks on four commercial vessels off the seashore of the UAE ’ s Fujairah port raised questions about maritime security in the Gulf .
3. Smuggling Smuggling at sea has been a problem for years. In recent years, port staff and port security have played a major role in the smuggling of illegal material such as drugs. The Port of Rotterdam has a speciate team of divers, the Dutch Customs Diving Team ( CDT ), whose aim is to find bootleg drugs .
With ports being large, international hubs with high volumes of shipments, and access to new markets, smuggling at ports is a common occurrence and a focus for port security .
Overview: International Ship & Port Facility Security code
The International Ship and Port Facility Security ( ISPS ) Code is an amendment to the SOLAS convention on maritime security—including minimum security arrangements for ships, ports, and politics agencies .
Essentially, the ISPS Code is a set of measures to enhance the security of ships and port facilities, developed in response to perceived threats in the wake of the 9/11 attacks in the US (IMO) .
After coming into wedge in 2004, it puts the responsibility on governments, shipping companies, ship gang, and port/facility personnel to “detect security threats and take preventative measures against security incidents affecting ships or port facilities used in international trade.”
 The ISPS Code is applied in Southampton, England, with signs prohibiting access to areas next to ships .
The ISPS Code is applied in Southampton, England, with signs prohibiting access to areas next to ships .
Enabling technology for port & harbor security
Old fashioned patrolling and crewed vehicles
Protecting ports the previous fashion manner involves human patrol. Marine patrols in harbors are normally done by a “port security unit”, which patrols the harbor by boat and typically deploy officers in the port areas .
Port security directors are responsible for identifying, addressing, and deterring threats against cargo vessels and cruise ships. Today ’ s patrol boats are designed for travel rapidly and maneuverability. They are capable of mounting special weapons and equipped with radar and sonar .
Electro-optical sensors, radar, integrated surveillance, tracking networks, computer systems
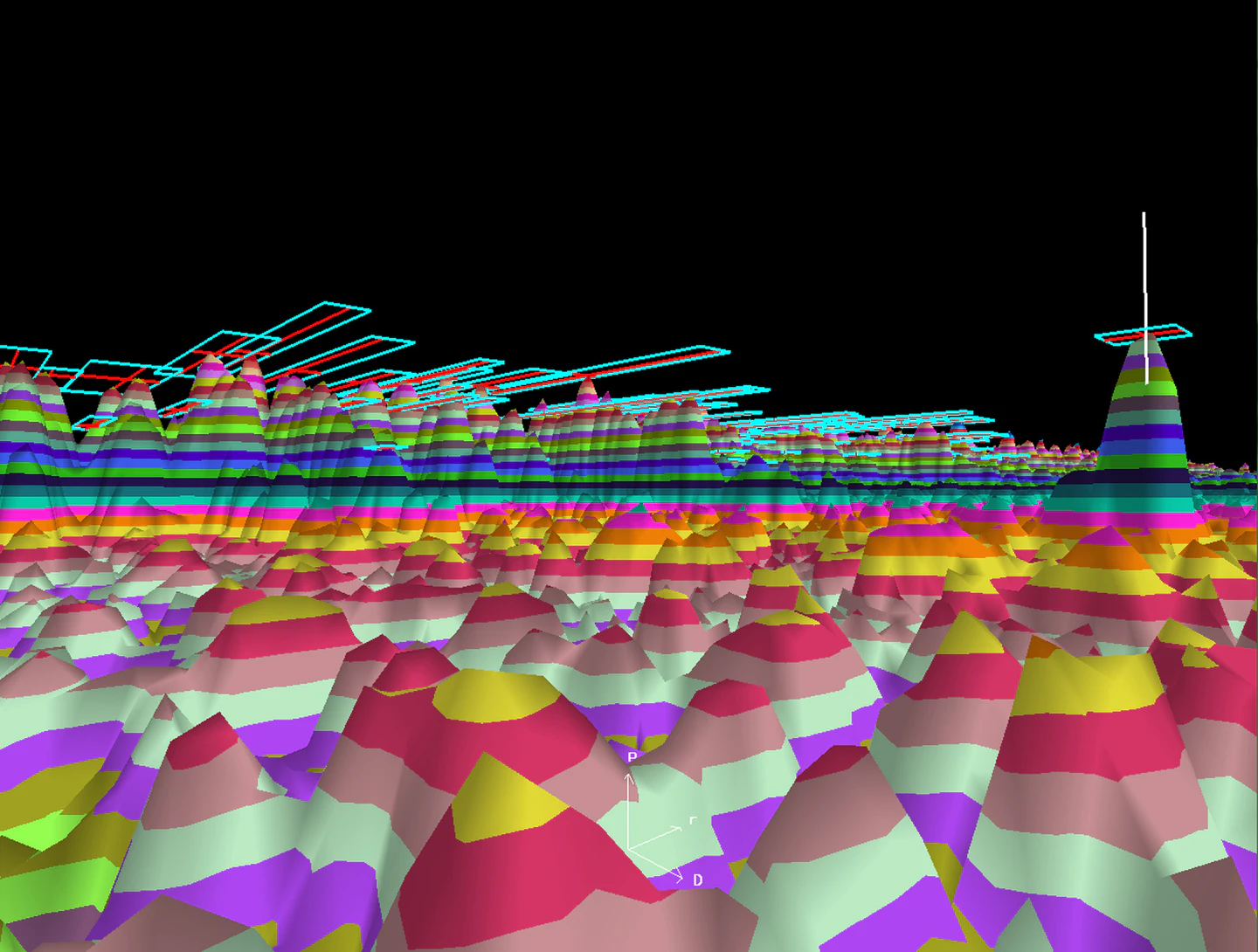 The Blighter C400 series coastal security radar has a built-in sea clutter filter to adapt to the changing sea and wave conditions mechanically. ( reference : military aerospace )
The Blighter C400 series coastal security radar has a built-in sea clutter filter to adapt to the changing sea and wave conditions mechanically. ( reference : military aerospace )
Newer methods of port and harbor security blend electro-optical sensors, radar, sonar, uncrewed vehicles, in addition to old fashioned human patrolling .
Blighter Surveillance Systems in Great Chesterford, England, is one such security system that produces electronic-scanning ( e-scan ) ground radar systems for counter-drone margin security, wide-area surveillance, and coastline security system applications .
It can detect a small wood gravy boat at ranges a far as 6.8 miles, day and nox, in heavy rain, dense daze, or even rough seas .
Leveraging geospatial products
The power of geospatial data and insights can enhance security approaches in order to keep waterways even safer .
For exercise, alleged “ black ” vessels—those that operate without radar transponders or that disable transponders, can be identified by fusing AIS signals from vessels with deep-learning-based ship signal detection methods .
first, you ’ ll need to process satellite images with car learning algorithms that detect ships before fusing the outputs with AIS data. If ships are detected but do not have corresponding AIS signals, they could be a campaigner to be a benighted vessel.
Read more: What is the Maritime Industry?
Read Webinar Recap : Why Satellite Imagery, AIS Data, and Machine Learning are Making Waves in Maritime Surveillance
 Dark vessel candidates are outlined in red, with AIS-transmitting ships outlined in orange .
Dark vessel candidates are outlined in red, with AIS-transmitting ships outlined in orange .
ready to build nautical security solutions ? Sign up to UP42 and access and analyze geospatial data today .







