Introduction
Oceans have long been the lifeblood of international deal and commerce. For more than five thousand years, humans have used rivers, lakes, and the seas to move goods from place to place promptly and efficiently. As civilizations continued to expand and better understand the strategic advantages of nautical trade, this custom accelerated. Initially logs bound together with r-2, vessel evolved into modest, carved, wooden vessels. Before long, the beginning major trade routes began to surface—and the ball-shaped nautical exile network was well on its way .
today, nautical exile contributes to one-fourth of US GDP, or some $ 5.4 trillion. No ball-shaped provide chain is mugwump of maritime transport, and most, in fact, are existentially pendent on it. Outside the United States, the ocean and ports worldwide moved around 80 percentage of global trade by volume and over 70 percentage of global trade by value. Global nautical trade continues to gather momentum ; in 2018, the industry expanded by 4 percentage globally—the fastest emergence in five years.
The maritime transportation sector besides is all-important for the success of early critical infrastructure sectors —specifically, the security of global energy systems. In 2016, more than 61 percentage of the earth ’ s sum petroleum and other melted department of energy supply was moved through sea-based craft. Maritime ship as a form of fare is essential for bulk tape drive of these natural materials due to the sheer volume of goods that must be moved and the competitive price sharpen the MTS offers. Maritime deal is substantive for supplying fuel to the ball-shaped economy .
A critical contribution of the United States ’ national security is the ability to project baron across the oceans ; the ship industry is a crucial cog of this wheel. Sealift—the ability for large-scale transportation system of troops, supplies, and equipment by sea—is the basis of US military ability protrusion, handling more than 90 percentage of the US Department of Defense ’ second ( DOD ) wartime transportation requirements. Sealift is the largest supplier of strategic mobility, a driver of economic prosperity during wartime, and a key subscriber to the US military ’ s global operational model. Sealift has manifested in assortment of ways, including shipping essential supplies such as petroleum and natural gas ( ONG ) to the Middle East in support of Operation Iraqi Freedom, or providing human-centered aid to the Philippines after brutal natural disasters, such as Typhoon Haiyan. The central function of sealift in enabling a diverse set of global operations—and the indigence to use maritime department of transportation to enable agile and strategic activity below the level of arm battle, such as exemption of seafaring operations, makes maritime security essential to US national security .
The Merchant Marine Act of 1920—better known as the Jones Act—further defines the relationship between the MTS and national security. Signed into jurisprudence just after World War I, the Jones Act seeks to promote and maintain the US merchant fleet to ensure that the country will have sufficient merchant sealift capacity in the event of a conflict or an incidental requiring the conveyance of large volumes of personnel and materiel. Among other provisions, it stipulates that any vessels transporting passengers or goods—even liquefied natural flatulence ( LNG ) —between united states ports must be built, owned, flagged, and crewed by US citizens or permanent wave residents. A century since the Jones Act ’ sulfur enactment, there are fewer than two hundred vessels that fulfill the legislative act ’ second criteria, many of which rely on subsidies from the government to maintain that capacity. Despite being one of the largest producers of natural boast, the United States is restricted by the Jones Act from shipping its own LNG to domestic ports on defiant vessels .
More broadly, nautical craft besides plays a winder function on the ball-shaped geopolitical stage for allies and electric potential adversaries. The United States is dependent on the ability to import goods from its allies via nautical conveyance : around 90 percentage of US sum imports arrive by sea. China, a near-peer rival of the United States, is acutely dependent on imports of petroleum and key resources such as iron to fuel its growing economy—goods that are about entirely transported through nautical craft routes. Maritime security is of vital sake to China, as the geography of the the Asia-Pacific region and, specifically, the strategically significant straits of Malacca and Singapore represent some of the most critical die points and active trade wind routes in the the populace —and ball-shaped nautical traffic has increasingly concentrated on these geostrategic choke points .
All of these factors have driven industry players to boost efficiency, automation, and outside management, in a word, more technology. The result however is far-flung adoption of software and hardware without adequate comparable management of the growing apparition of cyber risk .
Complexity begets insecurity
much like many early critical infrastructure industries, operational efficiency and profit drive maritime department of transportation. That drive has caused a shift toward an even more complex environment—and complexity begets insecurity. As the size of the global economy and its reliance on nautical activity have accelerated, the nautical fare sector has had to scale up its operations. Over the final fifty dollar bill years, the size and capacity of cargo ships have increased 1,500 percentage. In many ways, this dramatic scale-up has been essential for the diligence. It has allowed for an exponential increase in ocean trade and has driven prices down internationally. This rapid increase in size, however, has resulted in ships, and the MTS more broadly, becoming more complex .
The MTS is not monolithic. It ’ s a “ arrangement of systems ” composed of ships and ports, but besides the shipping lines, manufacturers, intermodal transportation operators, cargo and passenger handlers, vessel traffic control, and maritime administrators. Each of these is itself a system of systems with complex inner and external dependencies. While all ports have similarities, they vary in their ownership and tenant models, cargo- and passenger-handling capabilities, desegregate of civilian and military vessels, jurisdictional authorities, and more. similarly, all ships have some coarse functions, but are basically unlike in areas such as operation, cargo and passenger capabilities, and crew requirements. Applying regulations to vessels is frequently complicated by the fact that one ’ sulfur country of adjustment, ownership, and management might wholly be different, frankincense often requiring the coordination of several countries when adjudicating an incident .
Cybersecurity needs to be implemented and practiced by people engaged in all nautical activities—not just IT experts. The users of the MTS are a mix set : they work for a wide-eyed variety show of organizations, play myriad roles, and have varied professional backgrounds and experiences. A given body of water might see any combination of commercial, law enforcement/public condom, military, cargo, passenger, amateur, maintenance, and other types of boats—not to mention offshore drilling or weave platforms, weather and navigation buoys, and sea-based communication platforms .
For years, the nautical sector developed and deployed unique software and hardware, inherently limiting their connectivity and hazard exposure. however, the interconnected and data-rich populace of the twenty-first century has provided ship and port owners and operators with an opportunity to integrate more omnipresent IT systems with OT ones. These changes have led to increased automation, digitalization, levels of operational efficiency, and of course, better margins for owners and operators. Despite the MTS ’ s increasing deployment of OT and interconnected engineering, from ships to rigs to ports, the sector has not proportionately increased its concenter on cybersecurity .
Existing cybersecurity efforts in the MTS prove that it is hood to securely design, develop, and operate a amply connected environment—and even more so when these environments look different on a ship-to-ship and port-to-port basis. The MTS ’ mho increased reliance on converging OT and IT systems has introduced raw vulnerabilities and expanded the attack coat in the maritime environment—yet the stress and resources devoted to combatting these fresh threats still largely lags this development. In the integrated MTS, cybersecurity is only a good as the weakest link. It is critical that all links in the MTS logistic chain collaborate in establishing robust programs, properly prepare personnel, and maintaining the operational efficiency necessity for all parts to work as one. however, this is easier said than done .
The consequences of this disconnect—the deficit in cybersecurity investment compared to the addition in automation and digitization—have become increasingly clear in recent years. This much manifests itself similarly to early industries. Ransomware and phishing, two of the more common tactics and means of compromise globally, exist extensively throughout the MTS. In fact, all four of the earth ’ mho largest maritime transportation companies—A. P. Moller-Maersk ( Maersk, as it is known, is character of the A. P. Moller Group ), China Ocean Shipping Company ( COSCO ) Group, and Mediterranean Shipping Company ( MSC ) —have been hit by significant cyberattacks since 2017. Maersk, whose clientele operation systems were ravaged when the NotPetya malware unfold from an infect ukrainian tax-preparation software called MeDoc, spent more than $ 300 million to return to broad operations after ten days of rectify and redress. A report 400-percent increase in nautical cyberattacks during 2020, along with a 900-percent increase in attacks targeting ships and port systems over the anterior three years, point to a maritime diligence in the crosshairs of malicious cyber actors. Despite this, the industry and its regulators have only lento begun to move toward meaningful and systemic change .
Given the complexity and segmented ownership of the organizations comprising the MTS, a well as the compass of threats, there is no single authority or cybersecurity model that easily applies to the entire industry. A more modular approach is needed to take a collective reason of vulnerabilities and threats, and segment the MTS into individual systems that can support one another and/or leverage gains in early systems, and be addressed by policy makers. The approach ultimately must be holistic ; even if every part of the MTS was cyber secure, the interconnection of the subsystems might not result in a impregnable whole. A better understanding of the cybersecurity threat landscape, coupled with a segment position of MTS infrastructure, will be necessary to build a secure maritime world. This border on will allow developers, policy makers, owners, and regulators to match the best policy levers with detail maritime systems, and achieve better management of cyber risk across the stallion MTS .
Threats
The elements, pirates, and equal powers have challenged the nautical embark diligence for thousands of years. As the industry expands in size and integrates new technologies for add efficiency, the book of potential threats, and the consequences of likely dislocation increase exponentially .
In addition to the execution of new and insecure engineering, in the last several years new problems and worsening effects have challenged the nautical diligence in different ways. In early 2021, a Maersk vessel lost 260 containers overboard—about 2 percentage of its cargo—when the ship lost propulsion for less than four minutes in heavy seas. This was not an isolate incident ; both MSC and NYK Shipmanagement ( NYKSM ) have each had significant and comparable incidents since late-2020. Over the final ten, the World Shipping Council estimated that an average of 1,382 containers have been lost overboard per annum. While not all of these losses are linked to cyber incidents, they illustrate how much hazard exists in the ecosystem, and how the increased scale and complexity of the MTS have given rise to new concerns .
The COVID-19 pandemic is attest of the effects that a massive break can inflict on the MTS. The pandemic challenged the maritime diligence with port closures, a newly and shift demand landscape, significant supply-chain disruptions, and operational questions around health and condom. As a resultant role, for the inaugural time in decades, ball-shaped maritime trade wind actually dropped 4.1 percentage in 2020. No doubt, the pandemic besides will have long-run effects on the diligence that are so far impossible to quantify. COVID-19 forced states to think differently about their international relationships and trade patterns. The economic and security system consequences of such a large-scale break shocked many—and proved how unprepared the MTS is for such systemic challenges .
The most holocene and credibly most luminary single-event example of an MTS -wide disruption occurred when Ever Given, one of the largest commercial container ships in the earth, got stuck concisely after entering the Suez Canal in March 2021, blocking through traffic on one of the earth ’ sulfur interfering waterways. The vessel, at 1,300 feet ( 400 meters ) and about 221,000 gross tons, was stuck for more than six days and took several days of work from one of the world ’ randomness best salvage teams, a fortuitous high tide, and a dash of luck to unwedge. Although the cause of the incidental is believed to be a combination of heavy winds, the ship ’ second rush, and the vessel ’ south rudder size/alignment rather than a cyber attack, the bad luck caused ball-shaped economic dislocation. With 13 percentage of global trade passing through it every year, the narrow Suez Canal is one of the most strategically significant choke points in the world. The vector sum blockade of Suez Canal dealings held improving $ 9.6 billion in goods. once unstuck, the monetary value to “ refloat ” the ship landed at $ 900 million, to be followed by a quarrel over fiscal damages that ended in the seizure of Ever Given for closely four months by egyptian authorities .
The Ever Given incident illustrates the scale of disturbance that a cyber incident could have on ball-shaped ship, specially in geostrategic die points. It besides exemplifies the complexity and interconnection of the ball-shaped nautical system. ever Given was owned by a company in Japan, operated by a container shipping firm based in Taiwan, managed by a german company, registered in Panama, and crewed by twenty-five amerind nationals. The complex, interconnected, and multinational nature of the MTS makes coordination challenging and finger pointing around incidents common—but besides provides the diligence with a singular opportunity to leverage systemic and ball-shaped change if handled correctly .
There are precedents for high-consequence cyber events causing dislocation on the MTS, including in the United States. In November 2020, the Port of Kennewick was hit by sophisticate ransomware assail that forced operators to rebuild the Washington state port ’ s digital files from offline backup. This was not an isolate incident, but emblematic of a larger swerve .
The cyber-threat landscape in the MTS is like to that of other critical infrastructure sectors. Global Positioning System ( GPS ) and Automatic Identification System ( AIS ) obstruct and spoof, attacks on less-than-secure OT and industrial control-system ( ICS ) devices, human targets, myriad shipboard data and communications technology ( ICT ) systems, are merely some of the vectors that adversaries can and will use to attack the MTS. Ransomware, software supply-chain attacks, and social technology are a few common tactics, techniques, and procedures ( TTP ) that have been used against the MTS. Potential targets and victims throughout the MTS include ships, ports, passenger and cargo transportation lines, shipbuilders and nautical manufacturers, and others. It is a complex and inordinately moral force ecosystem that is difficult to defend. Cyberattacks represent an existential threat to the contemporary nautical diligence, the fluent operation of which underpins mod society .
Attackers as diverse as the MTS: Pirates to pwners
The MTS ’ s vulnerability to cyberattacks and its significance to US national security and economic stability have drawn from the carpentry an array of adversaries intent upon wreaking damage on the ecosystem .
barely as the MTS is not monolithic, neither are those posing a threat to it. There is no single profile of a threat actor and motivation for attacking nautical cyber systems. Sun Tzu ’ s well-known saying about knowing thy foe applies hera : “ If you know the enemy and know yourself, you need not fear the consequence of a hundred battles. If you know yourself but not the enemy, for every victory gained you will besides suffer a frustration. If you know neither the enemy nor yourself, you will succumb in every battle. ” Understanding where your risk is concentrated and who may look to exploit that risk are substantive steps to securing an administration ’ randomness systems .
Attackers in internet broadly fall within the following categories based largely on purpose.
Read more: A Man Quotes Maritime Law To Avoid Ticket
- Cybercriminals: Like criminals in the physical domain, cybercriminals are after financial or other tangible rewards; they are not ideologues, they want the cash. Cybercrime costs the global economy more than $1 trillion annually. Cybercriminals in the meitnerium engage in cyberfraud and are behind most ransomware campaigns.
- Cyber activists/Hacktivists: Philosophy, politics, social movements, and other nonmonetary goals motivate this group of threat actors. Typical tactics of hacktivists include defacing websites, launching protests on social media, and conducting acts of cyber vandalism; while often criminal in nature, the intent is rarely financial.
- Terrorists: The use of cybersecurity capabilities by a traditional terrorist actor could mirror an act of terrorism in real space—a violent criminal action, meant to intimidate or cause fear—and be motivated by political aims. This fear could directly, or indirectly, yield disruption with significant economics effects. Terrorrist groups also often engage in cyberattacks with financial motivations to fund other operations and help support recruitment.
- State-sponsored entity: State-sponsored entities: These actors often report to or receive support from nations or states. Acts of financial, industrial, political, and diplomatic espionage in cyberspace are the most common objectives for this type of entity. Intellectual property ( information science ) theft, in particular, costs the global economy more than $2 trillion annually by some estimates.
- State actor: Such actors have the resources and capabilities to conduct nuanced and sophisticated cyber operations. Although the most prominent state actors targeting the metric ton are Russia and China, both Iran and North Korea have proven capable of attacking numerous industrial sectors internationally. These operations normally work to advance strategic goals. There is no international consensus on a definition of “an act of war” in cyberspace and, therefore, it is unclear how defense treaties in traditional spaces influence hostile activities in cyberspace.
While an understand of the distinctions among threat actors can be useful in considering how to protect particular systems, a hard-and-fast categorization of any given cyberattack is often difficult because the lines differentiating these actors blur during any dynamic consequence. attribution is often a challenging and drawn-out process, and results can sometimes be probationary at best. many criminal organizations in internet, for example, have nation-state sponsors yet their actions are not considered state-sponsored .
Attackers have their own motivations, levels of capability, technical and fiscal resources, opportunities, time frames, and intents. The primary threat actors that have demonstrated a high capacity and willingness to conduct operations against the MTS and related critical infrastructure sectors fall within two categories : cybercriminals and state-sponsored actors. There are thin boundaries between these categories, given that some state-sponsored groups besides operate within long-familiar cybercriminal networks .
The main focus of cybercriminals is most much monetary profit. They target well-known organizations with big attack surfaces, prey on employees ’ miss of cyber awareness, and bearing for large monetary rewards. To accomplish these ends, ransomware has become one of the most coarse and populace forms of cyberattacks against MTS targets. Ransomware is used to paralyze a victim administration by encrypting its data and requesting a ransom, often to be paid into a pseudonymous cryptocurrency wallet. Most ransomware attacks are conducted by criminal organizations for their own profit, or to fund condemnable and terrorist activities in conventional outer space. Some other monetary motivations include reselling entree to the infrastructure, data obtained, or compromised computers on the darknet, a network using the Internet that requires license or special software .
Cyberespionage operations targeting the nautical community besides are common, chiefly in the form of intelligence gather and Internet Protocol ( IP ) larceny. Cyberespionage represents a center footing of action that can be valuable for both criminals and state actors. In March 2019, for case, taiwanese state-sponsored hackers reportedly targeted universities around the world, equally well as the US Navy and industry partners, in ordain to steal nautical engineering. China besides has an ownership and/or functional presence at dozens of major ports around the earth, providing a across-the-board capability for information gather on ports, vessels, and cargoes. Obtaining this type of access to MTS infrastructure can provide information of strategic significance regarding MTS cyber-physical security, information-system vulnerabilities, and operational information. furthermore, adversaries may consider breaching a network using zero-day attacks to maintain dogged access to MTS networks to affect or influence the infrastructure operations at the right time .
More sophisticated, state-sponsored attacks are just starting to find their way into the MTS, with incidents such as the May 2020 cyberattack by Israel on Iran ’ s Shahid Rajaee larboard in Bandar Abbas in reaction to Iran ’ s cyberattack on Israel ’ s water-supply system the previous month. Directed spoofing and jamming attacks on global put, seafaring, and time ( PNT ) systems by Russia, China, Iran, and North Korea are extra threats affecting the MTS a well as other transportation sectors .
Framing the challenge
It is imperative mood to establish at the beginning that there is no silver fastball for maritime cybersecurity. A history of honest-to-god shipboard engineering has been retrofitted to an era of interconnectivity, which has created a fracture and vulnerable maritime environment .
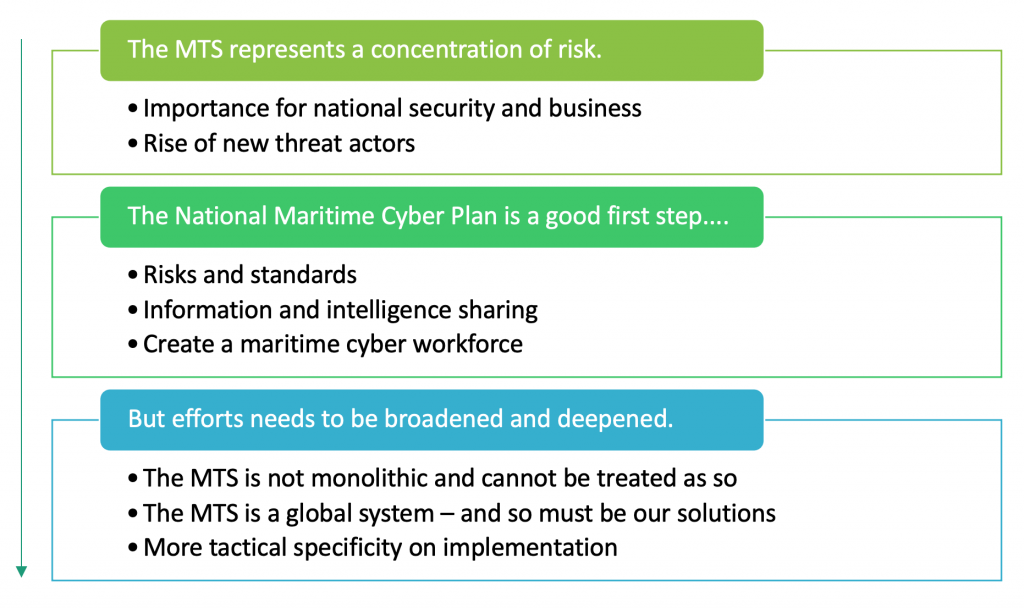 Figure 2. Next steps after the NMCP.
Figure 2. Next steps after the NMCP.
This report card is intended to deliver a more complete and operational plan to better protect the MTS by focusing on build up upon, broaden, and deepening the priorities put forward by the NMCP. The uranium politics took an significant inaugural pace in December 2020 when it released the National Maritime Cybersecurity Plan. The design aims to “ buy down the potential catastrophic risks to national security and economic prosperity caused by MTS operators ’ increasing reliance on IT and OT, while still promoting nautical commerce efficiency and reliability. ” To achieve this goal, the plan focuses on three keystone principles : risks and standards, information and intelligence share, and creating a maritime cybersecurity work force. The plan represents a significant step in the right direction and calls attention to many of the critical risks outlined in this report card. however, it lacks specificity on how to implement these three principles .
This report started by highlighting both the significance of the MTS and some of the most common and consequential threats to the MTS. now it pivots to discuss major drivers of risk to the MTS and three nautical life cycles—ships, ports, and cargo—and the key programs, vulnerabilities, and stakeholders in each. These sections are explicitly intended to extend the NMCP and identify areas of risk and electric potential advancement for policy makers and industry. The final section builds on the points of leverage identified in these three life cycles and offers specific recommendations to the United States, US allies, and the private sector to hand in glove reduce and better manage the system ’ s cybersecurity risks .
Explore the full report
This Introduction is region of a larger torso of contentedness encompassing the entirety of Raising the colors : Signaling for cooperation on nautical cybersecurity— use the buttons below to explore this report on-line .
The Atlantic Council ’ sulfur Cyber Statecraft Initiative, within the Scowcroft Center for Strategy and Security, works at the link of geopolitics and cybersecurity to craft strategies to help shape the lead of statesmanship and to better inform and fasten users of technology .
Learn more
Related content
Read more: Australia Maritime Strategy
relate Experts : Will Loomis, Gary Kessler, and Xavier Bellekens
image : Container ship leaving larboard .







