Table of contents
Human cyber risk
Systems cyber hazard
Maritime biography cycles
A “system of systems”: Understanding the MTS
TheMTS is a markedly complex “ organization of systems. ” This report card segments the MTS into three discrete systems—ships, ports, and cargo—each with its own biography bicycle. In this context, a animation cycle is an analysis of the progress of a specific unit of measurement or system within the maritime transportation system system. This incision discusses each of these system ’ s interactions, processes, systems, and vulnerabilities. These three systems do not capture the entirety of the MTS, but they embody the entities most cardinal to the sector and its security. This report seeks to highlight areas of risk and leverage for policy makers and the industry. The finish of this section is to illustrate the complexity and diverseness of these core systems and queer likely points of leverage for policy switch in each. not all actors, problems, and processes fall neatly into these systems, while others are elements in every system .
Before focusing on these life cycles, it is crucial to identify where the sources of systemic cyber risk exist in the MTS. Although these risks manifest themselves in different ways for the distinct subsystem of the MTS, they are all prove concentrations of cyber risk that one must consider when trying to protect the MTS from cyber threats .
In the late 2000s, the public and private sectors promptly adapted security system postures to address the threat posed by contemporary plagiarism. Years after addressing the menace, the security measures implemented then remain permanent wave fixtures of ships. This case demonstrates the nautical industry ’ second adeptness in reactively responding to crises, though it powerfully contrasts with the industry ’ s miss of proactive demeanor in addressing emerging cyber threats. There is a disconnect between the MTS and the countless potential cybersecurity threats it faces from a gamut of criminal enterprises and states. Every misconfigured device or user-restrictive system creates a new vulnerability that opportunist threat actors can exploit. This section aims to highlight some of the most common and consequential sources of systemic risks in the MTS .
There are two key categories of systemic gamble for the MTS : human gamble and systems risk. The captive of this section is to specifically highlight that vulnerabilities in engineering are an important gamble divisor in the MTS, but the human element—and the implicit in risk associated with humans working with building complex and challenging-to-understand technical foul systems—is just vitamin a critical .
Human cyber risk
It is a common mantra in security that humans are the weakest link in the defensive chain. however, humans are besides substantive to any solution. A big number of cybersecurity papers, conference presentations, and bodied studies focus on this dichotomy—so much so that the human fallible link is sometimes accepted as an changeless fact .
The cliché clearly implies that the exploiter is the weakest connect in cybersecurity with no citation of the graphic designer of the critical IT and OT systems. This seems to suggest that there is arrant information security—computers with locked down operating systems ( OS ), bouncy applications software, secure communications protocols, and hard encryption—that can withstand any attack, until a human user enters the picture. This is not an accurate description of computer systems. No OS is wholly fasten, because no developer can patch all know vulnerabilities during every plot hertz, much less those yet strange ; hence the big armory of zero-day exploits in the violent fair waiting to be launched. Software undergoes a frequent update and patch bicycle. This makes the uniform distribution of the latest “ up-to-date translation ” difficult within a big enterprise system. A communications protocol might be secure on paper, but then suffer from flaws in execution. indeed, many of these depend upon encoding schemes that are mathematically solid, but then weakened due to flaws in the software implementation or mismanaged keys. These vulnerabilities are not drug user created ; they are intrinsic to any system designed and run by humans .
This becomes even more challenge with a complex ecosystem like the MTS. Ships and ports are frequently operating with rotating crews that may not be amply familiar with their vessels, systems, and established cyber-hygiene practices. furthermore, crews may have varying levels of cyber literacy. A lack of digital culture and cyber literacy may benefit an attacker ’ s ability to gain data on a vessel and its systems or disrupt the vessel ’ s operations. More than anything, there is a critical indigence in the MTS to better understand the problems facing the sector. The easiest way to do this is more cybersecurity coach, department of education, and documentation for the MTS and its operators .
For the purposes of this report card, homo cyber gamble in the MTS divides into four discrete categories : social technology, lack of cyber hygiene, unauthorized access, and overcomplicated engineering .
Social engineering
As discussed above, humans are the most valuable, but besides the most vulnerable view in maritime cybersecurity, because they are the ones operating critical systems. Social engineering—or the handling of people—is one of the most common cyberattack vectors. Social-engineering methods include tease, electronic mail, voice mail, and SMS phishing ( and its variants ), malicious e-mail attachments, and pretexting, arsenic well as dim-witted misrepresentation. These techniques can be used by attackers to manipulate people into letting them gain access to personal computers of crowd members or operators in the hopes of infecting maritime systems .
Imagine an oil oil tanker chosen as a target by a hack group. In today ’ sulfur society, writes a foreman military officer working on commercial vessels, “ information regarding the vessel ’ s electrostatic and active ( course/speed/position ) datum, crowd composition, type and quantity of cargo, finish, captain ’ mho name, and other items of interest could be collected from the web. ” Attackers could search and exploit the social media networks of crew members, preferably the target vessel ’ south bridge team members, for extra information and deploy a spear-phishing campaign to harvest administrator-level credentials. social media networks and websites focused on professional groups and employment make these tasks easier. With that access, the oil tanker ’ s network would be within relatively easy clasp of the hacking group .
Ships are mastermind targets of many of these attacks. In May 2019, the United States Coast Guard ( USCG ) issued a Marine Safety Information Bulletin ( MSIB ) specifically warning commercial vessels about target cyberattacks where malicious actors, using e-mail addresses that appeared to be from a Port State Control authority, sought medium information such as crew members ’ names, personally identifiable data ( PII ) and protected health data ( PHI ), many times under the guise of COVID-19 management .
Holland America Line and Princess Cruises—both subsidiaries of Carnival Corporation—were victimized by a phishing campaign in May 2019, although it was not announced until March 2020. The adversary air phishing emails to employees to gain access to employee e-mail accounts, where it was able to reap employee and customer PII, including names, Social Security numbers, other government designation numbers, pass information, credit card and fiscal data, and PHI, according to the report .
Ships and ship lines are not the only likely targets. Bunker companies, fuel suppliers, shipping management companies, port operators, shipbuilders, and charterer companies could all be targeted and defrauded via email-based social-engineering attacks .
Lack of cyber hygiene
lack of basic cybersecurity best practices, or cyber hygiene, is a critical driver of risk for the MTS. Ship crew or interface operators might not be mindful of the risks of downloading files from the Internet, not enabling multifactor designation, clicking on electronic mail links, or the miss of anti-virus software and firewalls on their computers. An attacker may attempt to take advantage of a crew ’ s miss of cyber awareness and hygiene by sending phishing emails to its members. segregation between the crowd network and the bridge net may erode during an attack, creating more problems. Anecdotes abound about poor people cyber hygiene, including bridge crews implementing differentiated password controls merely to post the new passwords on sticky notes. such insecure practices highlight the challenges within the MTS when it comes to cyber awareness and hygiene .
With such enormous pas seul in missions and environments, ship and larboard managers often operate with rotating crews that may not be amply familiar with the larboard or vessel, its systems, and inherently the cybersecurity measures, or cyber hygiene standards, that accompany them .
Poor password practices are legion throughout the ICT -user community, and the nautical sector is no different. In August 2015, a ashen hat hacker reported on the ability to eavesdrop on Globalstar satellite communications systems that were both unencrypted and employing default passwords ; these Internet-connected devices could be found using the Censys or Shodan search locomotive. In October 2017, another whiten hat hack detailed how boater 900 VSAT systems—one of the marketplace leaders for nautical telecommunications—around the populace continued to use default passwords that could be found on Censys or Shodan american samoa well. In October 2018, a 19-gigabyte Navionics database, which contains details on more than 260,000 customers, was found unbarred on-line due to a misconfigured database that had no password. These are just a few examples of how the prevalence of hapless cyber hygiene can hamstring efforts for increased cybersecurity in the maritime knowledge domain .
Unauthorized access
Ships and ports are expansive and notoriously unmanageable to keep protected at all times. With multiple organizations, contractors, and entities working together on each ship and at each port, keeping rigorous oversight of access dominance levers can be difficult. This can manifest itself in two chief ways. The foremost is the insider threat. Whether the individual has a personal vendetta or is bowing to manipulation by another actor through blackmail or monetary incentives, insider threats are an authoritative threat vector. An insider attacker with inner cognition may be able to physically bypass access controls and restricted parts of buildings containing critical IT and OT systems, either using their own credentials or leveraging their cognition of the port and its systems. For model, an insider attacker could gain access to a command-and-control room and put key loggers at the back of computers using a dim-witted USB stick, allowing them to retrieve desired information on port systems, including logins and passwords. A 2018 reputation highlighted at least two instances of pervert access to deploy USB hitchhike drives with malware onto maritime systems. These actions can result in serious, long-run consequences .
The second gear chief manner of obtaining unauthorized access is through linking plug and all-important systems to insecure systems. Wireless networks have become the norm for web browse and daily operations in many industries across the globe. however, these networks, given their expanded practice by the MTS, are attractive targets for attackers to connect to essential systems in a larboard or on a vessel and potentially cause significant damage .
Overcomplicated technology
In late years, the nautical industry has pushed aggressively for technical integration, more automation, and new and better systems. Although some fresh systems make sailors ’ lives easier and more effective, changes can create significant modern security system problems. A dearth of qualified technical know-how onboard ships exacerbates technological complexity, but it is not the source of the problem .
In 2019, the USS John S. McCain collided with the Liberian-flagged vegetable oil oil tanker Alnic MC. After an extensive review of the incident, investigators determined that an excessively complicated touch-screen steer system and inadequate train were major contributors to the collision. The McCain helmsman said, “ There was actually a bunch of functions on there that I had no clue what on worldly concern they did. ” Afterward, a report by the National Transportation Safety Board ( NTSB ) said, “ the design of the John S. McCain ’ s touch-screen steer and thrust control condition system increased the likelihood of the operator errors that led to the collision. ” This exercise calls attention to the potential hazard of increasingly common overcomplicated technologies in the MTS .
Systems cyber risk
The MTS is comprosed of heterogeneous, complex, and frequently bequest systems. nautical systems are in a constant country of development. Assets are highly complect, include both stationary ( for example, land-based ) and mobile ( for example, shipboard ) infrastructures, and, in many cases, remain in about constant manipulation. Both fix and mobile infrastructures are interdependent and fretted. At their core, they are driven by processes and tools such as data flows, OT systems, OT end devices, ICT systems, ICT end devices, cloud infrastructures, networked nodes, communication systems, and condom and security systems. This profusion of systems and components ranges from generic IT and OT devices to more recess elements that are specific to the maritime ecosystem. Out of all these potential assail vectors, four stand out in terms of vulnerability, book of exploitation, and consequence .
Attacks on OT systems
The practice of OT—where embedded computers immediately control hardware—throughout ports and ships enables chic maritime systems. OT besides includes supervisory see and data learning ( SCADA ) systems, such as flow computers, transmit and transportation systems, and monitoring meters, which play a all-important function in the ball-shaped transportation of oil and natural natural gas. The engineering to support the evolution to smart maritime systems is promptly available and being quickly implemented in ports around the populace .
Cybersecurity protections, however, continue to lag behind the tempo of technical invention and execution. Although attacks on OT systems are calm relatively newfangled, cyberattacks targeting OT systems in the maritime sphere have increased by 900 percentage in the stopping point three years. Uncovered in 2010, the Stuxnet writhe targeted Siemens software that managed programmable logic controllers ( PLCs ) for centrifuges known for their consumption in irani nuclear research facilities. Upon infection, the controlling software would indicate normal operations on the display empanel, all the while instructing the centrifuges to spin at their utmost travel rapidly and causing them to self-destruct. Stuxnet was the first highly publicized software approach on hardware. Since then, ICS -specific attack tools have proliferated and are readily available on the Internet. The Stuxnet model besides proves how an attacker can exploit a vulnerability in the OT infrastructure or SCADA systems that could lead to fiscal or homo losses .
These effects can become even more drastic within the energy sector. In August 2017, Saudi Aramco and Qatar ’ second RasGas were reprise victims of the 2012 Shamoon virus that crashed 30,000 personal computers and closely reached into OT networks, with the goal of triggering an explosion. The Triton/Trisis malware, first found in the raving mad in 2018, specifically target OT systems and ICS at a Saudi ONG facility. Attacks at energy facilities have the potential to cause forcible effects such as explosions, threatening homo life and across-the-board fiscal harm. Such an attack at a high-volume port could be devastating .
Attacks on IT systems
Wireless networks dominate daily operations in many industries across the earth, and problems surrounding IT system vulnerabilities are common cognition. however, reports assessing the security of the nautical diligence indicate that open networks and weak encoding networks using the defunct Wired Equivalent Privacy ( WEP ), or other watery cryptanalysis algorithm, are still in use for Wi-Fi and Internet of Things ( IoT ) devices in the maritime world. such poor network security could expose essential systems in a port or on a vessel to attackers .
The maritime diligence ’ s digital transformation has led to widespread obscure adoption to manage personnel data, enterprise resource planning ( ERP ), customer relationship management ( CRM ), and other bodied functions. however, miss of mottle security computer architecture and scheme may lead to misconfigurations and unprotected application scheduling interfaces ( APIs ) that can be exploited by attackers to retrieve and collect key data. The SolarWinds supply-chain attack, publicly disclosed in late 2020, demonstrated the frailties of the software supply chain and the linchpin cloud technologies, equally well as the exploitable interconnection of a organization like the MTS .
Attacks on PNT systems
Ships trust on numerous ship-to-shore communication systems, geopositioning systems, and navigation systems to operate efficaciously while afoot and when entering and exiting ports. Attackers could jam geopositioning systems and ship-to-shore communications, or spoof the communications to threaten the safe navigation of vessels. These techniques could besides be used to gain a tactical advantage in a conflict .
Jamming and spoofing are far from hypothetical. GPS and AIS jam and spoofing are problems that have been widely documented for many years, and issues related to loss in signal, or flush a small aligning error, can be magnified within the relatively restrain space of a port, particularly when involving increasingly large cargo and passenger ships. In 2019, the nonprofit organization Center for Advanced Defense Studies ( C4ADS ) released a composition detailing russian function of GPS spoofing to achieve a diverseness of disruptive and strategic objectives. additionally, AIS is among the most critical systems in the nautical industry, as it allows for the exchange of vessel position and information alerts, yet it was shown to be systemically insecure angstrom early as 2013. The potential effects of compromise PNT are significant, as modern ships rely heavily on these satellite- and radio-based systems for seafaring .
Ransomware
Although it is not a specifically target system like the former three categories, ransomware represents a threat to all types of systems in the MTS. According to the US Cybersecurity and Infrastructure Security Agency ( CISA ), ransomware is an “ ever-evolving shape of malware designed to encrypt files on a device, rendering any files and the systems that rely on them unserviceable. malicious actors then demand ransom in central for decryption. ” Ransomware groups effect companies to pay a ransom to regain control condition of their systems and/or to prevent the escape of large quantities of data .
Ransomware has targeted the nautical industry in the past several years, as it has many early industries globally. The vogue began in dear in 2017, when the NotPetya operation took Maersk ( and hundreds of other organziations around the world ) offline, as discussed above. In 2018, COSCO ’ s north american subsidiary company, COSCO Shipping Lines, was hit by ransomware, shutting down its operations and IT systems for days. In 2019, hackers used the Ryuk ransomware to disrupt the entire IT network of the port, ampere well as respective ICS systems used to transport and monitor cargo, for roughly thirty hours, completely halting operations. 2020 was a wake-up bid for the maritime diligence about the harms of ransomware, as Carnival, CMA CGM Group, Garmin, Hurtigruten, Port of Kennewick, and Toll Group were all victims of ransomware attacks. The interconnected nature of add chains and the distinguish actor set in the MTS make the industry particularly vulnerable to ransomware and more likely to pay off ransoms in order to avoid sustain disruption of these supply chains. To help mitigate the ransomware threat to the MTS, ship and logistics companies must improve IT hygiene and electronic mail security to harden networks against park ransomware tactics .
Maritime life cycles
It would be impossible to individually address each subsystem in the MTS in one go. This report focuses on three key subsystems : ships, ports, and cargo. While all ports have similarities, they besides are unlike in terms of their possession and tenant models, cargo- and passenger-handling capabilities, blend of civilian and military vessels, jurisdictional authorities, and more. similarly, all ships have some common functions but are different in terms of their intended determination, operation, design, crew requirements, and regulative practices, among other things. The life cycle for the transportation system of cargo is flush more speciate ( as are the key systems relied upon ), depending on what type of good is being transported. The approaches to building a cyber defense within the MTS must be adenine varied as the elementary components within it .
In addition to the unlike subsystems in the MTS, there besides are a broad diverseness of players that are essential to the operation and security of the global MTS. As with the subsystems, it would be extremely challenging to address all of them ; alternatively, the postpone below maps their roles and responsibilities. For more information on specific players, please see Appendix 1 .
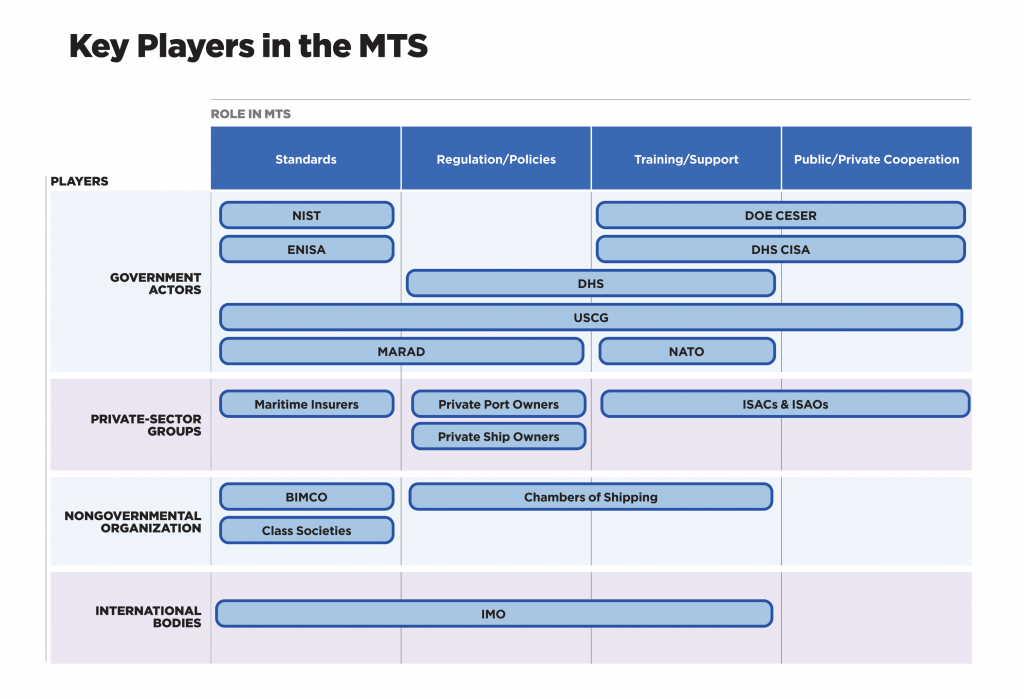 Figure 3: Key players in the MTS.
Figure 3: Key players in the MTS.
The pursue sections examine three unlike segments of the MTS —ships, ports, and cargo—to demonstrate the interconnection of the system of systems that comprises the MTS. These three subsystems of the MTS are both the most critical and the most embrace. Each segment highlights some of the key processes and cyber risks involved—and identifies points of existing programs and relationships that can be leveraged and capitalized on to better secure the MTS .
Cybersecurity and the life cycle of a ship
Ships are the center of the maritime diligence. By most historical accounts, the trade inheritance of advanced ocean-going vessels can be linked to the austronesian peoples as army for the liberation of rwanda back as 1000 BCE. today, ships handle about 80 percentage of global barter by volume and more than 61 percentage of melted energy deal. They besides play a key character in US national security and baron projection. To address this increase demand, the development of ships and ship over the ages has changed dramatically in terms of the oscilloscope of ocean-going travel, international laws and regulations, an sympathize of the sea and upwind, navigational methods and technologies, ship design, and so much more .
This development besides has driven invention in ship-based systems and their associate cyber risk due to growing engineering integration and remote access by vessel shoreside management, vendors, and other substantive third base parties. Ships illustrate the challenge of securely designing, developing, and operating a fully connected environment—even more so when these environments look different from ship to ship. Distinct functions require specific IT and OT systems, meaning that securing each ship looks inherently different .
Protecting ships needs to be a priority. All the entities involved in the life hertz of a ship—from the architect and builder to the hustler and cargo company—are susceptible to cyber threats and therefore partner in this security. This section unpacks the nuances of a ship ’ south life bicycle with respect to cybersecurity by walking through how ships are designed, constructed, operated, maintained, and decommissioned. Each section highlights some of the key processes, players, and cyber risks involved, and identifies points of existing leverage that key actors can capitalize on to better secure the MTS .
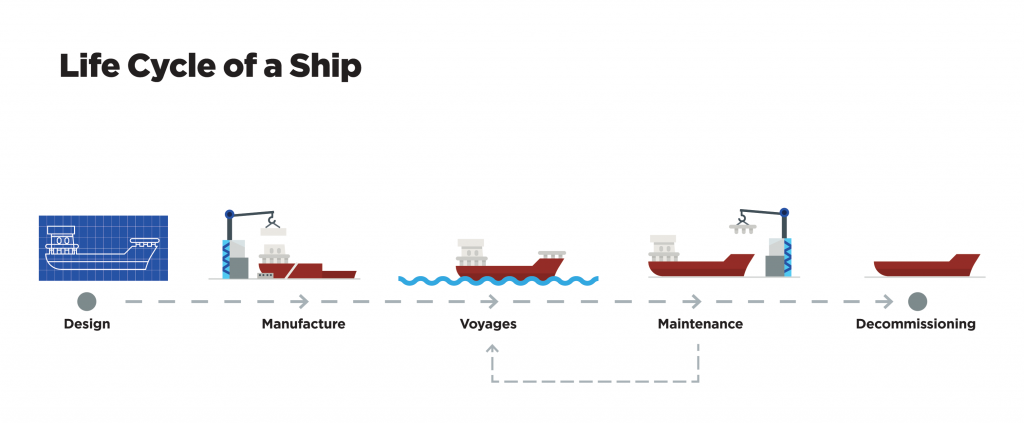 Figure 4: Life cycle of a ship.
Figure 4: Life cycle of a ship.
Design phase
While the chief focus of a embark ’ sulfur blueprint is related to seaworthiness and operational functionality, it is only in the last one hundred years or less that transport designers have had to address nonmaritime shipboard technologies, such as those shown below :
- Networks for intravessel communications and control, including everything from security, engineering, operations, and entertainment to cargo handling, ballast, intercoms, and integrated bridge systems; and note that cabling systems are directly impacted by the choice of communications devices and their protocols, affecting some aspects of ship design
- External communications networks for navigation, situational awareness, email, entertainment, radar, weather, and satellite phones, among other things
- intelligence community and OT equipment for vessel and cargo management, such as LNG transport
 Figure 5: Shipboard technologies.
Figure 5: Shipboard technologies.
These new systems are substantive for operation—yet they besides must be designed and integrated securely. The calculator and telecommunications networks, for example, do not merely necessitate communication media laid out over the ship, but need to be designed and segmented in a plug fashion, necessitating cable layouts that support the secure design. Cybersecurity flaws and weaknesses introduced during the design phase and found during the shipbuilding phase will be harder and more expensive to fix .
technical standards for the design of ships are maintained by the classification, or classify, societies, nongovernmental organizations that set and maintain technical standards related to the invention, construction, and operation of ships and offshore structures. These standards normally focus on elements of the transport such as the ship ’ south hull, propulsion and steering systems, exponent generation, and other systems related to a vessel ’ south operation. however, these standards imprison when it comes to the cybersecurity of not alone these core systems but besides the on-board IT and ICS systems. securely designing every aspect of a ship and its systems is a complicated endeavor, and it looks different for every ship due to factors such as size and determination. Certain organizations like the International Maritime Organization ( IMO ), the Baltic and International Maritime Council ( BIMCO ), and the European Union Agency for Cybersecurity ( ENISA ), a well as the National Institute of Standards and Technology ( NIST ) Cybersecurity Framework, put forth guidelines on best practices when it comes to cybersecurity ; by choosing not to be prescriptive, however, they have remained excessively wide-reaching to implement on a sector-to-sector basis, let alone ship to ship. Private-sector entities should work with these standards organizations to make them both easier to implement and more tailor to best practices .
The homo element of cybersecurity besides is a potential risk vector during the design phase. IP larceny is a very real trouble for designers and shipbuilders. In the past, there have been numerous incidents where foreign actors were able to get their hands on critical invention IP, which has put operators in compromising positions. Adversaries having confidant cognition of ship design, connectivity, and the inner workings of critical ship systems makes defense street fighter, if not impossible. An adversary with entree to ship design blueprints could even insert little changes, leading to flawed or even catastrophically debatable fabrication .
In summary, although the design phase seems relatively simplistic, it is actually the begin detail for cyber risk in ship-based maritime systems. Security in design is not fair for software development—and efforts are necessity to build awareness that the ships all-important to the national economy and security must besides follow the rationale of whole-of-life-cycle cybersecurity .
Construction phase
The construction of a ship at a shipyard is a tightly organized, complex choreography of the parts and people required to build a ship. As most commercial ships are built in shipyards located in South Korea, China, Japan, Italy, and elsewhere, the installation of equipment and initial cybersecurity is a commitment of trust between owners and builders. tied today, it remains an incredibly labor-intensive process with limited automation in the shipbuilding process ; the construction of some of the largest vessels nowadays can take up to two years. Managing speciate parts, auction block construction, and the skilled labor pull ( for example, electricians, carpenters, metallic workers, and engineers ) provides many opportunities for a cyberattack to cause huge delays and fiscal loss. unauthorized modifications to the employment schedule can mean that necessity workers are not available when needed, causing construction delays. A cyberattacker using intelligence gleaned from the design phase could credibly manipulate the arrange of parts to either delay the requested arrival date or to introduce the function of counterfeit or differently bad components. Extraordinary wish to manage the provision chain is necessity to maintain the accurate time required to get a transport built on time .
 Figure 6: Ship under repair in Hamburg shipyard.
Figure 6: Ship under repair in Hamburg shipyard.
There are many ways to compromise this process. A consider act of sabotage or initiation of an accidental flaw during the design phase of a ship will result in a weakness in the ship ’ s integrity. A badmouth actor could introduce such a flaw and alter the design plans. A humble change to a blueprint can cause one forget of a ship, where obstruct construction is employed, to fit improperly with the main vessel. This becomes a more significant problem for onboard systems and software. Imagine an insider inserting a Stuxnet-type hardware vulnerability into a critical onboard system during assembly. As the ball-shaped shipping diligence continues its efforts to increase automation, improve efficiency, lower costs, and adjust to an increasingly digital-driven earth, there is an ever-increasing reliance on software to monitor, calculate, and execute critical tasks aboard a vessel—and with this reliance comes more hazard .
additionally, the 2020 Sunburst operation has shed newly light on the risks associated with software and software supply-chain compromises. Ships trust on software to do everything from voyage to control the inner ballast systems, which much lack adequate security shape and thus expose them on the Internet. The Sunburst campaign has shown that operations targeting these types of systems, which in this casing compromised some of the biggest players in the secret and public sectors, are going to become more and more the average for twist actors with nuanced strategic aims. Preventing systems entirely from these types of compromises is a chump ’ mho errand : there merely are not adequate resources in the MTS to do it. however, by better understanding the software in use and the concentration of risk on a transport, operators can better identify and mitigate potential cyberattacks as they surface. It besides is authoritative that the international maritime residential district, the individual sector, and governments communicate extensively about these types of threats. They need to openly share attacker tactics and technical strategies for moderation, and facilitate personnel exchanges and other forms of cross-sector and cross-national collaboration to train professionals who can understand the problems and potential threats to the MTS from a assortment of perspectives. This type of many-sided cooperation is critical to the identification and extenuation of systemic risk in the MTS .
Operations phase
A transport spends the majority of its life at sea, going from port to port. As in the structure phase, a ship ’ sulfur operation requires a complex coordination between shipping lines, ports, departments, and agencies involved in crowd acquisition and management, investors, schedulers, regulators, maritime administrators, cargo handlers, fuel and ship ’ sulfur stores suppliers, and more. While operate in and around US waters, ships may interact extensively with the USCG, which runs point on both police enforcement, incident reception, and regulative natural process for the MTS .
supply chains are an all-important anchor to keeping a vessel on the go and operate efficiently and efficaciously. Ships are floating cities, complete with comparably complex computer and communications networks. A ship ’ s inner net interconnects with the countless systems required to keep the vessel adrift and the external network keeps it operating efficiently at ocean, as seen in digit 5. There are an calculate seventy-five to eighty thousand commercial vessels on the seas today. While ships are susceptible to about all kinds of cyberattacks in the operations phase, one of the biggest threats are those to navigation systems, particularly jam and spoofing the Global Navigation Satellite System ( GNSS ) and v. A belittled erroneousness in PNT time can cause a big erroneousness in status ( for example, one microsecond timing mistake can cause a vessel to be off status by 1,000 feet, or 305 m ). Issues related to PNT systems have a huge potential impingement on the MTS, particularly when it comes to ship operations. Attacks on seafaring system can be individually disruptive by delaying a single ship ’ south arrival at a port or globally disruptive by causing a vessel to run aground, possibly blocking a port or waterway for days or longer. GPS spoof has become therefore coarse in some parts of the world that many consider the system unreliable and frequently resort to navigation by other means. The MTS must move quickly and aggressively to find and employ technologies to detect, fight, and mitigate the effects of AIS and GPS spoofing. In addition, the US government and DOD need to build a bouncy PNT system that is repellent to attacks on satellites .
There are multiple exploiter levels for gang accessing shipboard IT engineering. Crew members access information systems for transport operations systems specific to their subcontract function or personal use. Ships officers have significantly more far-flung custom, with higher levels of access to more systems. elder officers have access to all ship systems, particularly those assigned to shipboard and external communications functions. The embark ’ s maestro, chief IT officer ( if there is one ), and possibly others, may have the responsibility to update calculator systems, enforce software patches, and maintain graph updates and other navigation systems. This access is in line with normal cybersecurity practices around minimum necessary access ; however, these deviate levels of access can create their own problems. Depending on the level of access to these systems, an insider attacker with intimate cognition of the security protocols could physically bypass access controls to access restricted areas containing critical systems. Compromises of IT systems can besides come off as less significant than they actually are, which can lead to ship operators opting to not disclose an incidental. It is essential to define what qualifies as a maritime cyber incident and set protocols to inform the proper public- and private-sector actors, namely the USCG and electric potential ports of bid, that an incidental has occurred. In recent years, the US Coast Guard has made essential steps to establish impregnable and crystalline disclosure programs. however, we must besides recognize that these programs are still relatively nascent – specially when compared to early sectors like fiscal services – and indigence to be far developed and matured with fourth dimension and extra resources .
additionally, crews onboard often lack a basic understand of cyber hygiene. Yes, batten passwords have been installed on key systems, but that is undermined if the raw password is placed on a gluey note next to the system access point. Social mastermind attacks, phishing, ransomware, and other incident operations that directly target users are rampant across the entirety of internet, and their impact on the MTS should not be underestimated. To combat this, there is real motivation for lend train and education. There are US programs within the Department of Energy ’ randomness ( DOE ) Office of Cybersecurity, Energy Security, and Emergency Response ( CESER ) directorate, the Department of Homeland Security ( DHS ), and the USCG that focus on cybersecurity. however, stream and future risks require more collaborative discipline across the public and private sectors, and more maritime-specific cybersecurity department of education. Although it seems like a small step, proper education on nautical cyber threats and cyber hygiene best practices can make a serious difference when it comes to mitigating risk .
Another potential vector for harm is the tape drive of malware from port to port, and to other ships, by an infect vessel. A 2019 simulation by the Cambridge Centre for Risk Studies explored the potential impact of a computer virus carried by ships that connected to port networks. In one worst-case scenario in the simulation, the malware effectively destroyed the cargo database at fifteen ports in China, Japan, Malaysia, Singapore, and South Korea, which would cause equally much as $ 110 billion in damages—of which 92 percentage ( $ 101 billion ) would be uninsured .
Securing these critical systems and processes during the operations phase is challenging. This presents one of the largest concentrations of hazard in the MTS. Some of this gamble is the leave of lax security-development practices on the function of the private sector and inconsistent deployment of systems previously that have resulted in insecure and hard-to-defend systems. Standards bodies and regulators, such as NIST, USCG, and nautical insurers must work with the private sector to better understand and protect critical systems. however, it besides is essential to work to streamline communication internationally on key extenuation strategies and vulnerability disclosures, and invest in better education for users so that they can better understand how to protect their own systems. One key facet of this is the rate at which disclosures are identified, made public, and addressed. In the past, found-yet-unmitigated vulnerabilities have remained unaddressed for american samoa long as a full year due to poor responses to vulnerability disclosures from vendors. This can not continue : the MTS must double down on a indigence for confidence through a press for policies of accelerate, transparency, and receptiveness around vulnerability disclosures .
Maintenance phase
A vessel needs to move in near constant motion to produce maximal gross. Keeping the transport operate at high capacity demands care, including :
- Routine cleaning and repairs, such as repainting the hull or accommodations, or replacing worn lines and chains, and often performed while the ship is underway or at port
- Periodic refurbishment and upgrades to ship operational systems, which can include retrofitting new OT or information technology systems, and requiring a short time at a maintenance yard
- A complete overhaul and rebuild, requiring an extended stay in dry dock, for hull modification, installation of new OT or information technology systems, a new superstructure, or even an entire repurposing of the vessel
even small delays in this process can yield a meaning impingement. The ripple consequence includes the impact of how soon a ship under care can get back out to sea and when the sustenance adeptness is available for other vessels .
The cybersecurity threats during the maintenance phase are like the structure phase, namely, fiscal fraud, IP larceny, hacks into the work-schedule and parts-ordering systems, and supply-chain issues. however, these threats are specially prevailing in the maintenance phase because maintenance—often conducted in foreign ports—creates an opportunity for foreign-based malicious activity .
Decommissioning phase
At the end of a vessel ’ second life, owners decommission and, ultimately, disassemble, them. The steel used to build a vessel—that which has value—is recycled, while the rest is discarded. ship breakers must cautiously handle any hazardous materials used in construction, such as lead-based paints or asbestos, to prevent an environmental incident. Dismantling facilities are by and large near urine and increasingly found in developing countries, primarily in Asia .
Cybersecurity threats in this phase are alike to those of any business. Cyberfraud is of particular concern, as money changes hands for the sell and buy of parts and materials. Attacks on scheduling systems and databases can cause delays in the decommission process or mismanage of the ship ’ second component pieces .
Key takeaways and points of leverage
Ships represent a concentration of cyber risk in the MTS. They possess a complicated and distinguish gamble model that can be challenging to address holistically because of the diversity of missions and systems and the opacity and miss of fundamental understanding of the threats. To push toward stronger cybersecurity postures for ships, this section identifies three points of leverage that represent key beginning steps for this inaugural .
first, distinctly ships are systemically insecure : so far a one-size-fits-all approach path to security standards would not help solve what is inherently a vessel-specific problem. The ball-shaped fleet is not monolithic—different transport owners and operators have unlike missions, unlike onboard systems, and frankincense, different risks. multinational organizations like the IMO, in close partnership with the secret sector and the course societies, must continue the existing NIST Cybersecurity Framework Profiles campaign to provide clearer, more differentiated guidelines on cybersecurity best practices that can be implemented for particular subsections of the larger ecosystem .
moment, there is a current miss of situational awareness and collaboration in the MTS that erodes our ability to respond to emerging threats and extenuate risk on both a sector-wide and subsystem-specific footing. It is substantive that the MTS expands and clarifies existing protocols and programs to streamline and incentivize information commute and vulnerability disclosure. Whether it be through personnel exchanges, collaborative train exercises, or other forms of cross-sector and cross-national collaboration, more teamwork is essential to push fore extenuation of systemic risk in the MTS —and it must be deeper than good information substitute .
last, there remains a significant need for more educate across the public and private sectors, ampere well as more maritime-specific cybersecurity education. proper department of education and prepare on maritime cyber threats and cyber hygiene best practices can make a serious difference when it comes to mitigating risk. The United States and its identify international partners must leverage preexisting trail and educational programs to invest in a compulsory platform for operators thus that they can better understand how to protect shipboard systems and, therefore, lower the systemic risk for the MTS .
As mentioned, ships are the heart of the nautical industry. Yet, the varied nature of missions and systems sets them up for bankruptcy and makes the undertaking of widespread adaptation of cybersecurity best practices a daunting one. It is impossible to increase the security of the broader MTS without addressing this .
Cybersecurity and the life cycle of a port
Retired Admiral James Loy, a erstwhile USCG commanding officer, is wide credited with making the wry observation, “ If you ’ ve seen one interface, you ’ ve seen one port. ” Ports change widely in terms of ownership and management, the blend of civilian and military vessels and operations, the interconnection of IT systems by larboard operators and tenants, types and skill sets of available personnel, intermodal Transport connections, the bulk and type of traffic, cargo, and passengers, types of vessels that can be accommodated, and more. That said, a port is a microcosm of all aspects of the MTS activities and processes. It is a business community, and thus it has many of the same cyber issues as any early clientele community. port operators and the USCG need to focus on securing a swath of maritime-specific systems that are critical to its effective operations. This is not an easy or cheap objective. It will take a significant investment of money and human resources from the uracil government to achieve .
Cyberattacks on ports share some similarities to those previously discussed relating to ships and shipping lines. Attacks frequently target both IT and OT systems, or the users who employ or have access to these systems. These incidents include phishing, electronic mail scam, cyberfraud, social engineering, inner threats, ineffective disposal of data devices, IP larceny, and physical attacks on data memory and data systems .
The chief function of a interface is to provide an interface between sea and land transportation system. On the nautical side, ports need to accommodate many types of ships, including cargo vessels ( carrying liquid/dry majority goods, oil and natural gas, containers, or general cargo ), fishing boats, passenger and fomite ships, and port overhaul boats ( such as tugs and fender vessels ). Each character of vessel has specific moor and loading/unloading requirements and specific dock-facing systems—and frankincense, each will have unlike types of terminals and irregular repositing facilities at the port. The sheer volume and variety of necessity systems at ports make cybersecurity challenge and resource intensive. A one-size-fits-all approach will leave systems wildly unprotected .
The port or politics vessel traffic-management service plays a vital function in the legato passage of vessels into, out of, and around the port sphere. The assorted nautical terminals on land treat cargo and passenger onloading and offload, and the port ’ mho storage facilities provide at least irregular storage of cargo before a ship ’ s arrival for loading or upon unloading. Cargo and passengers transfer to other fare modes at the port, including automobiles, buses, trucks, railroads, inland watercourse vessels, and airplanes .
Ports maintain support services for all these activities, such as moor, cargo handling, passenger and crew accommodations, exile within the port facility, data network and telecommunications, and everything else needed to maintain the menstruation of larboard operations. base hit and security services are authoritative at the port to protect personnel, passengers, and cargo, peculiarly in this age of ports as targets of larceny, terrorism, and other hostile acts. The safety circumference of a interface is not fair on land, of course, but extends out to waterways within the port ’ s area of operation. Cybersecurity is a key element of port security—but so besides is forcible security .
ultimately, the port must maintain services for the versatile agencies and other entities that have authority over some aspects of port operations. This includes the harbormaster ( or the USCG ’ s Captain of the Port ), the interface administrator, governmental organizations ( such as the USCG, customs, immigration, and other bound protective covering agencies ), shipping companies, fiscal institutions, and unions. If military vessels have a presence at the port, a affair between military and civilian authorities besides will be introduce .
none of the functions described above occur in isolation. A lot of data moves around a port between the port authority, ships, ship operators, governmental agencies, cargo handlers, intermodal transfer companies, fiscal institutions, and more. As many cyberattacks have shown, when data stop act, everything stops moving .
Unlike a transport that has classifiable life-cycle phases, a port is in continuous operation with many coincident data flows, where hub of activities intersect with other segments of the MTS and beyond. From a cybersecurity perspective, consider these ICT segments within a port including the port margin, information and communication technology, industrial control systems, positioning, navigation, timing, and ships .
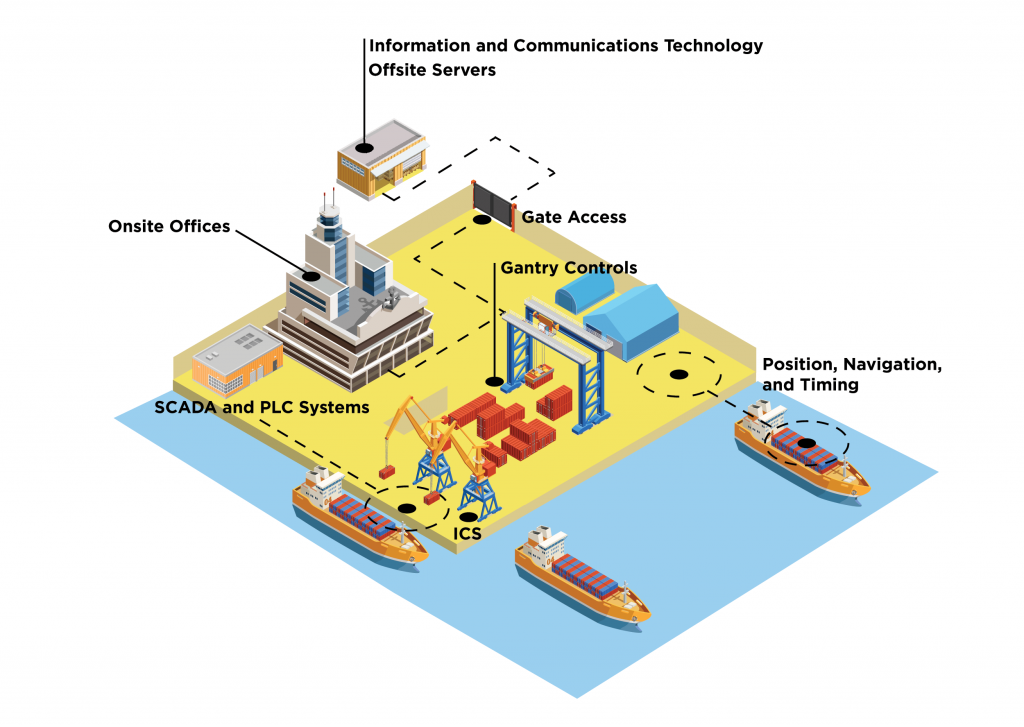 Figure 7: Key elements of a port.
Figure 7: Key elements of a port.
Port perimeter
The port perimeter includes all gates for ingress and emergence, the secured land-based limit, and the line depicting the water boundary of the port ’ s authority. The circumference represents the first line of larboard security. It is at the gate and other entry points where employees, passengers, crew, contractors, vendors, and others enter and exit the port. These employees or visitors likely embark and leave in automobiles, buses, trucks, and rail cars with passengers and cargo. apparent motion detectors, cameras, radiation sickness sensors, alarms, and early access-control mechanisms monitor the motion around the gates and fences, and complect via networks. The port ’ s security organization, maritime administrators, shipping agents, ship operators, immigration and customs officials, cargo handlers, logistics managers, and others must manage the drift of crew, passengers, employees, cargo, ships ’ stores, and goods for the port. All these activities rely on databases and other applications that are interconnected and accessible via the Internet .
After 9/11, port management and owners were entrusted to develop and maintain security, which has been described as overwhelmingly focused on physical security. however, physical security is not merely reliant on guns and guards—it besides is critically dependent upon network-attached cameras, sensors, alarms, and other detection equipment. These devices connect back to a central localization where security personnel can check their condition. Sites such as Censys and Shodan allow anyone to search for ICS devices that are accessible via the public internet. many attested reports of hacks on web-based cameras, vulnerable satellite communications systems, security devices, and IoT devices at ports ( and on ships ) have been recorded. Vulnerabilities in these systems, if exploited, could well hide an emerging physical security terror such as the access of an unapproved person. As suggested earlier, supply-chain issues affect ports in two ways, with the port being character of the distribution slope of the ball-shaped supply chain a well as being a consumer. The necessary access—granted to a “ trusted ” clientele or trading partner—can hedge both the cyber and physical defenses of a port. This is specially apposite, because ports interact with so many contractors and independent businesses on a daily footing. Maintaining a proper circumference and being able to monitor forcible bearing enable cyber and forcible security—yet back it when breached .
Information technology (IT)
The MTS is dependant upon information and ICT, and this is possibly no dependable than at a interface. The constitution and management of all the moving parts at a larboard command complex algorithm to ensure the most efficient flow of people, ships, cargo, supplies, and equipment. machine learning ( ML ) and artificial intelligence ( AI ), coupled with ICT, are increasingly critical to modern ports, peculiarly as they adopt smart-port technologies .
The servers hosting information at a port pull off all functions found at any clientele, from marketing, finance and payroll, and public relations to logistics, operations, and personnel management to ship scheduling, supply-chain management, and coordination with regulators and other authorities. All systems aspects that handle personnel files, including the immigration status of passengers and crowd, are here. These systems that manage port functions are a collection of servers at the port itself, third-party services, and cloud-based services. secure telecommunications are substantive for the movement of information between all these entities .
Cyberattacks against port IT infrastructures employ the like vectors as seen elsewhere in the MTS, namely, hacks into server systems, exploitation of software, and handling of computer users. If a bad actor can not break the port ’ s network defenses, a following step is to try to enter by posing as or compromising the network of another company that has legitimate access to the interface ’ south network. One particularly fruitful nerve pathway for attacks that covers all these targets is the provision chain, where ports play two significant roles. First, embark plays an integral character in the movement of goods in the ball-shaped supply chain. Second, ports themselves receive a enormous number of products and goods for use at the larboard and on ships, and therefore besides is a consumer at the end point of ball-shaped add chains. Both roles in the provision chain create cyberattack vulnerabilities .
Industrial control systems (ICS)
Port and transport practice of ICS, aboard OT, is contribution and parcel of the creation of the smart nautical systems of the future. Faster, smaller, and cheaper calculator processors, communications networks, and sensors are enabling the Maritime IoT. ICS, coupled with AI and ML, is at the heart of the emerging automation in the MTS, including operations that are remotely controlled or remotely accessed, computer assisted, and in full autonomous. OT-based automation augments port operations with ache cranes and gantries for the onloading and unload of cargo, digital lines, and smart ports that can check and report wind speed and focus, water temperature, depth, and other information throughout the port ’ s waters and berths. Autonomy is finding its room into docking systems, tugs, port vehicles, and drones. It is besides essential for the energy sector ; ICS is all-important for the transportation of anoint and natural gas between refineries and ports, and ports and ships .
 Figure 8. Smart cranes and gantries change the look and operations at ports.
Figure 8. Smart cranes and gantries change the look and operations at ports.
Attacks on ICS are peculiarly unreassuring. CISA ‘ s Industrial Control System Joint Working Group ( ICSJWG ) produces a steady flow of bulletins related to attacks on the IoT infrastructure and each new vulnerability found. One of the difficulties securing many ICS devices is the minimal drug user interface of the embedded devices and frequently limited capability to alter device settings .
Maritime cyber threats in this kingdom include attacks on the software controlling gantries and the placement of containers, both on the vessel and in the port ’ s staging areas. Attacks on ICS and autonomous vessels, vehicles, drones, and other systems at a port are great unknowns ( for example, autonomous docking systems and autonomous tugs ), potentially altering data-gathering computers and sensors on these systems to negatively impact their operation, including causing catastrophic failures .
This is particularly authoritative for the tape drive of oil and natural boast. There have been several past noteworthy cyber intrusions targeting shoreside OT energy networks including the 2017 Saudi Aramco hack, and the 2018 discovery of the Triton malware. With ONG networks, the stakes start higher and merely go up from there. The DOE ’ s CESER division has worked, often in partnership with the US home lab, on moderation strategies for these types of operations. however, more can be done—and the private sector should play a significant function as it comprises the owners and operators of the majority of the systems in interrogate .
The Cyber Security Agency of Singapore ( CSA ) offers a step in the right guidance with its newfangled Operational Technology Cybersecurity Expert Panel ( OTCEP ). With the inaugural meeting set for September 2021, the OTCEP will bring in concert a diverse and multinational group of experts on OT to strategize how to better protect these critical systems from attackers in the nautical domain. These types of initiatives should provide a road map for international collaboration on this subject going forward .
Positioning, navigation, and timing (PNT)
PNT functions are essential to the successful operation of about all aspects of modern society. GPS and other satellite-based navigation systems offer essential position information for all forms of transportation system, from pedestrians and bicyclists to ships and airplanes. Timing signals from GPS satellites are essential for the proper operation of all digital network infrastructures, including mobile call and telecommunications, television receiver, power grids, and ball-shaped deposit networks. GPS is besides a key component to AIS, vessel traffic-management services ( VTMS ), scheduling and directing vessels to a berth, surveying, dredging operations, position of aids to navigation, chart updates, container traverse, and more .
PNT -related issues can have a huge likely impact on ports, particularly when it comes to ship operations and port management. Attacks on the navigation arrangement could cause a ship to crash or run aground, blocking a port or watercourse for days or longer. The C4ADS report indicated that the Port of Shanghai, for model, suffered undetected GPS spoofing incidents starting in 2018 and had three hundred such events occur on one day in July 2019 alone. Maritime Safety Administration ( MSA ) boats are patronize targets of GPS spoof : one was spoofed 394 times in a nine-month period .
AIS spoof is another ongoing threat in port areas. Smugglers much spoof AIS signals from legitimate vessels to escape signal detection by the authorities. The Shanghai MSA reports that vessels carrying banned sandpaper and annoy accounted for twenty-three collisions or allisions on the Yangtze River in 2018, with the loss of fifty-three lives. In 2019, a tanker suspected of smuggling anoint was sending cloned AIS signals and, reportedly, rammed an MSA patrol boat to evade capture .
clearly, bad actors will continue to exploit PNT systems in the coming years—yet the secret sector has even to produce a dependable alternative. Without a more fasten and defendable product, it is arduous to persona this trouble decrease .
Ships
While vessels in passage constantly fill ports, they besides have fleets of local vessels, including fly boats, tugs, local commercial fishing and cargo vessels, public safety and law enforcement boats, and recreational boats. As central hubs connecting with thousands of ships, relationships of common hope much exist. however, this faith is likely undue and flush dangerous, and the safest approach is a zero-trust model .
When it comes to cyber incidents in the MTS, the lack of a consistent threat matrix far justifies this safe approach path. As an exercise, the Shen Attack composition highlighted the electric potential for a travel to vessel to infect a port ’ sulfur network and how that infection could then spread to other ships on the net. The interface ’ sulfur network, then, becomes an amplification steer in the spread of malware. To avoid this, ports must properly report and silo ( or disconnect ) any infect ship and its systems until resolving the compromise. however, the introduce miss of report standards leads to an corrosion of the situational awareness that is substantive for interface law enforcement and incident respondent. The MTS needs to be a mistreat ahead of these types of threats—not a step behind. The individual and populace sectors need to work together to clarify incident report standards. Ensuring that key actors are aware of a potential gap helps address compromised systems accordingly and contain the bedspread .
Key takeaways and points of leverage
Ships are critical to the MTS as they are the independent hub for commercial interactions in the industry ; yet they existentially rely on certain sets of insecure systems to facilitate these interactions. To push toward stronger cybersecurity postures for ports and their effect processes, this section identifies three points of leverage that represent key first steps .
first, the swerve volume and assortment of necessity systems at ports make keeping a proper cybersecurity position a challenge and resource-intensive finish ; a one-size-fits-all approach will leave many systems unprotected. As with ships, stakeholders across the international public and private sectors must work in concert to set guidelines and best practices for cybersecurity hazard management at ports—but this is not enough. Actors seeking to improve security in the MTS must besides work directly with procurement bodies, such as the Federal Acquisition Security Council ( FASC ), to incentivize the purpose of more secure systems. If systems are insecure before they always even become share of the MTS, ports are fighting with one hand tied behind their back. Second, port security is stuck in a post 9/11 world. In 2021, the physical security of ports and the goods stored there is not barely reliant on guns and guards—it is besides critically dependent upon the ability of network-attached cameras, sensors, alarms, and early invasion detection equipment to help identify homo threats. It is critical that port operators, a well as the USCG, advance an effective security system mentality at ports that utilize resources properly to secure ports from modern threats, not outdated ones. ultimately, it is crucial to limit the spread of potential infections between ships and ports. The Shen report card, described earlier, highlighted the potential for a travel to vessel to infect a port ’ south network and amplify the spread of malware, which represents a systemic terror to not entirely a port but to the ball-shaped maritime ecosystem. By strictly tiering and defining what qualifies as a significant nautical cyber incident and streamlining protocols to inform the proper public- and private-sector actors in the case of an incident, the electric potential hazard and extreme blast spoke of more twist incidents can be reduced .
In compendious, ports are a microcosm of the larger MTS and sit firm at the affection of the nautical industry. One individual port may interact with hundreds of ships and thousands of individuals in a single day. These challenges make cybersecurity at ports a difficult and ever-evolving situation .
Cybersecurity and the life cycle of cargo
The transport of cargo—whether it be tourists on a cruise ship, towering stacks of containers on a transoceanic transport embark, or oil and natural gas sealed inside the hull of a tanker ship—is the cardinal purpose of the MTS. Outside of humans, ships nowadays carry every conceivable type and combination of goods, in many form factors, including inland and near-coastal barges, container ships, bulk-goods cargo vessels, roll-on/roll-off ( ro-ro ) ships and ferries, vegetable oil tankers, and LNG carriers .
The volume of cargo transported, a well as the locations from which it ships to and from, is alone an expansive discussion. An interactional map, created by Kiln and University College London ’ s Energy Institute, illuminates the diverseness in missions and destinations when it comes to the ball-shaped drift of cargo in the MTS .
Matching the diversity of cargo is an ever-widening range of cyber threats facing nautical cargo conveyance. many types of cyberattacks can be directed at cargo, either while it is in place or in transportation system. These attacks share many similarities with those on ports and ships—especially because the transportation of cargo is existentially dependent on ports and ships for transportation. Depending on the type of cargo, the types of ship- and port-based systems used for transport, and which part of the life cycle of cargo the attackers are targeting, different segments of the systemic cyber threats facing the MTS can manifest themselves as the biggest drivers of risk for cargo .
The rest of this section unpacks cargo ’ s life sentence bicycle in the MTS by looking at cybersecurity risks posed on commercial containers and ONG products in storage, at their originating port, at sea, and when they reach their final destination. Neither intends to provide a complete painting of the type of cargo transported throughout the MTS ; alternatively, they serve as demonstrations of where this risk can be most condense .
For commercial container shipping, consider the life sentence motorbike of what ’ randomness called an intermodal container, due to its standard size and design so that it can travel by hand truck, train, or transport. The twenty-foot equivalent unit ( TEU ) is the standard measure of a ship ’ second cargo-carrying capacity, and broadly corresponds to a single truck or train cable car .
 Figure 9: Unloaded cargo containers at a port.
Figure 9: Unloaded cargo containers at a port.
For the transportation of ONG products, a barrel—defined as containing 42 US gallons of liquid product—are the chief unit of measurement. There are many systems that play a separate in transporting ONG products, however, there are four that are most essential to the achiever of the exile process : tank monitor and storehouse systems ; terminal transfer and pumping systems ; loading racks ; and automation master systems, instrumentation, valving, and metering. These systems enable critical processes throughout the cargo life sentence motorbike, and the sections below address them in detail where applicable .
Despite differing types of cargo, the act of transporting either a commercial TEU or a barrel of ONG starts well before entering the MTS at one port and ends well after leaving the metric ton :
- Storage (Origin)
- Port of Embarkation
- In Transit at Sea
- Port of Debarkation
- Storage (Destination)
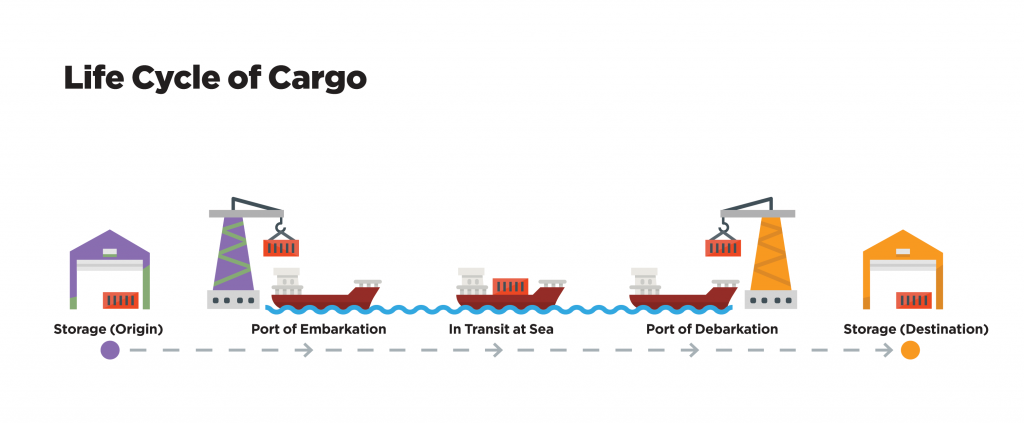 Figure 10: Life cycle of cargo.
Figure 10: Life cycle of cargo.
Storage
The initial memory adeptness, whether it be a warehouse, tank farm, or something more niche, represents the first check for any cargo beginning its travel through the MTS. Goods in the action of shipping need safe and dependable memory to protect them from potentially damaging threats such as the elements of nature, damage and end due to careless handle, pilferage, etc. Depending on the character of cargo, these goods can frequently spend unfold periods of clock in warehouses, exposing them to a diverseness of threats .
Most modern repositing facilities are technology marvels that use bombastic swathes of engineering to facilitate key processes such as sensitive or temperature-controlled units, transmit, and inventory management, among other roles. The bluff complexity of these facilities creates significant opportunity for cyberattacks during the cargo ’ s life cycle. This can manifest in several ways. First, there has been a meaning billow in automation in storehouse facilities. Technology intended for fabricate nowadays assists with distributing assets and prepping and packing them for enchant in repositing facilities across the area. Increased automation has besides driven an increase in the necessitate for collaborative and distant management tools. Some smart warehouses use drones or robots for moving and packing goods. Warehouses besides come in many shapes and sizes. public warehouses are government run and used by both public- and private-sector actors, while individual warehouses are frequently owned by a shipper or a ship note .
For TEUs, there are many cyber-enabled attacks on IT systems that can impact the shipper, shipping wrinkle, and warehouse anterior to a container formally entering the MTS. As an model, financially motivated bad actors have proved capable of the electronic manipulation of both cargo documentation and handling systems. additionally, cyberfraud, fiscal fraud, false bills of ladle ( much used to cover up smuggling of illegal or contraband goods ), cargo larceny, and more can all happen by attacking the shipper ’ s data centers and IT infrastructure, and manipulating inputs such as what is supposed to go where. IP larceny besides is a factor at warehouses and ports, where an intruder can learn about the contents of containers, vitamin a well as the transport agenda and early data that might have value to a rival or adversary .
OT systems in storage facilities are besides vulnerable to cyber exploitation. Often, perishable products, such as food that needs to be chilled, or barrels of oil and natural gas, which must be carefully transported and stored, can be held in these warehouses. research confirms the being of adversary capability to disrupt the types of cooling systems used to chill a container of erratic goods, frankincense causing spoil of the contents and disrupting key shipments before they have even left their initial localization. Although there have been limited examples of these types of attacks on storage systems in the fantastic, they represent a threat vector that is a hazard throughout the life cycle of cargo and a potential target for adversaries in the approximate future .
The human element is a huge challenge for storage angstrom well. Like ports, storage areas can be a moral force use environment with employees, independent contractors, and external agents ( such as truckers ) moving in and out all day. Imagine an overseas manufacturer or nation-state badly actor entering a partake government warehouse to place a malicious device into containers bound for a ship with which to launch a broader cyber operation against the MTS. The homo element of cyber hazard clearly exists for warehouses and it can not be mitigated without a better sympathy of cyber hygiene and best practices .
For ONG products, the risks associated with intersection repositing at this decimal point in the process looks slightly different. memory and the security system of ONG cargo while at remainder is a critical business. Yet, unlike TEUs, they are rarely placed in designate warehouses. alternatively, ONG products are frequently stored in boastfully oil terminals at ports, which are basically large groupings of tanks used to store anoint and natural boast before it is loaded onto vessels for transport ( fig. 11 ) .
 Figure 11. Tank farms dedicated to storing crude oil are present at numerous ports in the US.
Figure 11. Tank farms dedicated to storing crude oil are present at numerous ports in the US.
Monitoring the condition of these tanks is essential to the security and fiscal health of the transport process. Tank monitoring systems allow users to check fluid levels in multiple tanks, across multiple sites, from a remote control location—preventing users from overfilling tanks, which is not only dearly-won but has been known to potentially lead to fires and explosions. These systems will notify users when a wide variety of problems occur, including changes in volume and fluid levels—allowing owners to assess their product, no matter where it is geographically located. however, this overlap between critical guard need and remote-monitoring capabilities makes monitoring systems a electric potential flash point for cyber gamble. By shutting down or manipulating the functionality of these devices, an adversary could disguise malicious activeness until it is besides deep to stop the potentially explosive effects .
It is genuine that many of the potential threats discussed here, and throughout this cargo section, have even to be immediately exploited by an adversary—at least to the authors ’ cognition. however, the consequences of these potential vulnerabilities underline the fact that stakeholders in the MTS need to be looking forward, not backward. A reactionary approach path to addressing cybersecurity threats will not lone misallocate the limited funds for cybersecurity that do exist, but besides leave operators unprepared for the tactics of ever-evolving adversaries .
Originating port
once cargo is ready to begin its journey, it goes from the initial storage localization to its port of departure via caravan, truck, or some other human body of transportation. This process looks different for TEUs versus ONG products .
first, TEUs : after some degree of inspection and confirmation, information about the container is entered ( normally mechanically ) into the port ’ s computers. The container then gets directed to a denounce sphere, where it stays until the proper time to be moved to the designated position and loaded onboard a transport. A container ship typically carries hundreds or thousands of TEUs. This requires a complex jell of algorithm to optimize load and unloading sequences and accurate embark locations, ampere good as managing the ship ’ mho ballast. These algorithms need to determine a container ’ south placement based upon the stallion voyage of the vessel and know at which catch on the travel the container will be offloaded, special requirements for the TEU ( for example, ensuring that a container is placed in a power bay, if required ), and the load balancing needs of the ship. This complexity is the root causal agent of insecurity at this stage. additionally, depending on the character of cargo, the loading work looks different ; nonstandard containers and early types of goods may go through a slenderly different process .
The stage dancing of cargo ( and unloading ) containers is a result of messages exchanged between the ship agents, stevedores, tonnage centers, and transport ’ mho master/cargo officer. The cybersecurity risk here can be huge. Attacks on the loading/unloading software, IP larceny, cargo manifest, bayplan/stowage information, ICS /OT controllers, and more at ports can cause a misloaded vessel and damage to cargo or the ship itself, a well as early potential affects .
Attacks on ICS and OT systems can be extremely disruptive at this stagecoach, very like to ports, causing potential misloading or misstaging of cargo containers. A misloaded ship could be particularly vulnerable to rough seas, leading to the loss of containers overboard or other negative effects. such attacks can besides damage or disable gantries, cranes, TEU containers, port vehicles, and vessels. The research firm Trend Micro demonstrated a comparable operation in 2019, proving the ability to take control of several big commercial cranes. Although these types of attacks have yet to wide manifest in the MTS, they represent the following step of electric potential exploitations in the MTS and a authorize case of the physical and economic effects of a potential approach. port owners and operators need to work closely with the u government to better understand their cyber hazard profile in the MTS and begin to implement best practices that can start to reduce this system risk .
This action looks distinctly different for ONG products. Before any ship plan to transport ONG can get afoot, terminal transfer-line systems must move the product from the port ’ mho storehouse facilities to the shipside tanks. This collection of pumps and pipelines allow vegetable oil and lifelike gas to safely and directly travel from storage tanks at the port to storage tanks near the ships .
once safely transferred shipside, the ONG merchandise is loaded onto ships using loadout racks. This structure, located at a terminal or bulk plant, consists of a chopine and a load arm designed for use in loading the compartments of an oil-transport vessel. These automated systems actually load the cargo onto the ships themselves. Throughout this serve, operators use metering systems to enable operators to monitor and manage the vegetable oil and natural accelerator that they are transporting to ensure the proper quality and volume. In some ways, consistent meter is one of the most crucial parts of this summons, as intersection measurement is one of the clearest determinants of tax income for the diligence and thus has a direct impact on profit .
To automate the work of tanking and loadout, these systems typically utilize automation platform technologies such as distribute control systems ( DCS ), base hit instrumented systems ( SIS ), programmable logic controllers, work automation controllers ( PAC ), distant terminal units ( TRU ) and other distant input/output hardware ( I/O ). Newer engineering besides has allowed for radio plain instrumentation and communication enmesh networks that are designed for industrial area classifications in the ONG environment. many of these systems for the death two decades have ethernet network-based communications on the processors, workstations, and net hardware and have migrated from traditionally separated systems over the years to enterprise IT networks to be even more incorporate .
Owners and operators rely on these systems when moving ONG from ports to ships. however, the past has revealed flaws and operational vulnerabilities with these crucial systems—and the risks are high. First, these critical systems can be susceptible to insecure remote-access processes, leaving them potentially vulnerable for exploitation. This is a hood problem to solve, as outside access—the ability to analyze and review the operation of systems remotely, which is essential for ONG transportation—is critical in a nautical sphere when it comes to safety and care. however, this connectivity besides inherently broadens the approach come on for these systems. second, like the rest of the MTS, cyber risks exist during the entirety of the conveyance march due to a lack of cognition of cyber hygiene in the broad operator community. One exemplar is the use of Wi-Fi networks by gang, both onboard and at ports, which can open modern avenues for exploitation and lateral motion through social engineering attacks. finally, alleged technical school run overrepresents another potential menace vector for these systems. Although many critical ONG systems are designed to be batten, the development of ship ’ second technology over time can result in newly levels of connectivity and greater exposure .
It is critical that the ICS systems that enable the guarantee exile of ONG goods are better protected. Imagine the implications of a system break during fuel transfer between a transport and a interface, resulting in an environmental spill, a meaning explosion, and electric potential passing of life. The biggest problem when it comes to mitigating these cyber risks is that organizations do not know where to begin, and this applies to humans ampere well as systems. The NIST Cybersecurity Framework is a good start, but the MTS needs more specificity, particularly when it comes to bulk energy operators. The north american Electric Reliability Corporation Critical infrastructure Protection ( NERC CIP ) standards are a effective road map and should be implemented more holistically across ports that rely on these critical systems to transport ONG products .
In transit
once loaded up, containers and other types of cargo are then transported from the origin port to the destination port on a road that could include intermediate ports, where other containers have scheduled offloads and added cargo that needs load .
The cybersecurity terror for cargo at ocean is minimal, but not nonexistent, and it often aligns with the cyber threats discussed for ships above. A cyberattack on a cargo vessel can immediately impact the cargo in theodolite. A refrigerate container, for exercise, might lose baron, thus causing spoilage of the contents. Safety and monitoring devices on a bulk oil carrier wave might be turned off, affecting the stability of the vessel and putting lives and cargo at risk. A cyberattack on the loading/offloading systems of an LNG carrier could cause a catastrophic failure of the cool mechanisms necessary to maintain the dependable enchant of the fuel. A cyberattack on the shipboard arrangement that causes an electric cutoff at power bays could allow a flash-point increase near a container with flammable vapors .
A malicious actor could introduce a rogue communication device in a container to launch a cyberattack on a ship ’ s or port ’ randomness network. With some major liners exploring IoT -enabled containers, which customers can access remotely, the container itself may become a aim vector. In most cases, ship operators do their best to ensure proper cybersecurity practices are followed, including network cleavage. however, the connectivity of these fresh smart containers, if accessed while onboard, could widen the attack airfoil for ships. This could lead to compounding effects in the mathematical process of a ship ’ s seafaring or communications systems or, in a worst-case scenario, connect to networks at the ports to which the ship visits—leading to even more lateral apparent motion. Although this type of operation may be rare, it lone serves to further highlight the interconnect nature of the cyber threats to the MTS .
One thing to consider during this segment of cargo transportation is the ability for a cyber operation to affect physical operations. For the nautical knowledge domain, the most obvious exercise is pirates. A 2016 character report known as “ Roman Holiday ” illuminates this gamble. During this operation, pirates raided an anonymous ship company multiple times. This is not irregular—pirates are known to raid commercial cargo transports. The outlier in this case, however, was that these pirates seemed to know precisely where the highest valued goods were on the ship without having to search for them. It was late identified that the company ’ south content management system—where the ship ’ s bills of lading lived—had been compromised. In this case, the lone negative effects were stolen goods and a loss of net income. however, if you exchange the commercial goods in this scenario for, say, nuclear processing components, the likely risk of cyber-shaped physical operations becomes abundantly clear .
Destination port
once the cargo reaches its concluding address port, the trip at sea is complete and it is time to unload. The process at the finish port is like that at the originating port, but in overrule. petroleum and natural boast must pass through the same chain of systems discussed above to unload. Containers to be unloaded from a vessel want to be accurately identified, and unloading algorithms control container removal and scaffolding. The process looks slightly unlike depending on the cargo, but in all cases there is a critical reliance on engineering to do indeed .
As ahead, messages exchanged between shipping agents, stevedores, tonnage centers, and the ship ’ sulfur master/cargo officer dictate the stage dancing to unload the containers. information about each container must be entered ( normally mechanically ) into the port ’ s computers. Customs inspections need to be managed and bills of lading need to be reviewed and inspected .
Although the fire vectors look similar for unloading ships and loading them, the likely uses for adversaries can look distinctly unlike. between 2011 and 2013, a condemnable group was able to gain access to the Port of Antwerp ’ s IT systems. They capitalized on this access by using it to identify and intercept the containers their international partners had filled with illegitimate drugs. When their access was finally discovered and mitigated, the criminals physically broke into the facility and downloaded malware that allowed them to continue their operation unmonitored. not only does this illustrate how cyber and physical action can intersect in the maritime domain, but it besides shows how comparable risks to the cargo exile procedure can manifest in diverse ways for malicious actors throughout the life bicycle .
ultimately, containers and other goods are placed onto appropriate intermodal conveyance to be taken off-site and transported back to a shipper or warehouse. The cybersecurity menace during this stage can be significant as well. Attacks on the loading/unloading software or ICS /OT controllers can cause a stir in the counterweight of a vessel or injury to cargo ( or the embark ). Falsified or altered bills of lading can besides cover up smuggling of illegal or contraband goods, or larceny of cargo .
Destination storage
once the cargo has been taken off the ship and processed at its destination port, it is time to make its way to its final examination address. Full containers and early types of cargo finally arrive at a distribution warehouse, where they are emptied, sorted, categorized, and the contents distributed to other forms of transport to their ultimate destination. ONG products are transferred from their ships into fresh tanker farms before they are finally loaded onto other forms of tape drive and shipped to their concluding destinations .
The information security issues hera are very broad and similar in about every way to those discussed above. By attacking the shipper ’ s critical systems, bad actors can accomplish cyberfraud, fiscal fraud, false bills of load ( much used to cover up the smuggle of illegal or contraband goods ), IP larceny, exploited OT and IT systems, cargo larceny, and more. Cyberfraud and fiscal crimes hit shippers through imposter orders or money transfers directed to the warehouse, intermodal Transport companies, or the port itself. The actual larceny of cargo can be directed at warehouses and ports via bogus orders, bills of ladle, or shipping instructions .
Key takeaways and points of leverage
Cargo is the fuel that drives the MTS and the connection tissue between ports and ships. This means that the department of transportation of cargo is the main profit driver for the MTS ; yet the department of transportation of that cargo is besides reliant on the ability of operators to mitigate many of the same cyber threats facing both ports and ships. To push toward stronger cybersecurity postures for the transportation system of cargo, this section identifies three points of leverage that represent key first steps .
first, the fare of cargo is an inherently complect business. It can not happen without ports, ships, and shipping companies, not to mention the owner of the cargo. Shipping companies must work with ship and port owner-operators to help them facilitate the execution of best practices and standards, and share information to protect their bed course .
second, industry leaders need to stop being reactive when it comes to cyber threats and start looking forward. good as our systems continue to evolve, then will the tactics and capabilities of our adversaries. Many of the likely cyber vulnerabilities to cargo discussed in this section have not however been exploited by malicious actors ; but waiting until they are would be a critical mistake. key stakeholders in the MTS, including the public and individual sectors and academia, must follow the exemplar of programs like GridEx, Project Evergreen, or the United Kingdom ’ s Cyber-Ship Lab, and bring to address these next-generation vulnerabilities before they are utilized by our enemies .
finally, there is a critical need to better protect the storage and department of transportation systems that are vital to the transportation of ONG products. These systems look different from others in the MTS and have potentially destructive consequences from as so far unexploited vulnerabilities. Implementing the NERC CIP standards for these systems would be a good first step—but it can not be the last one .
In summary, cargo is not only the main economic driver of the MTS but besides inherently relies upon ships and ports on a day by day basis to make certain it can reach its concluding finish. This reliance leaves it vulnerable to a wider variety of threats .
Explore the full report
A system of systems is partially of a larger body of content encompassing the entirety of Raising the colors : Signaling for cooperation on maritime cybersecurity— use the buttons below to explore this report on-line .
The Atlantic Council ’ s Cyber Statecraft Initiative, within the Scowcroft Center for Strategy and Security, works at the link of geopolitics and cybersecurity to craft strategies to help shape the demeanor of statesmanship and to better inform and impregnable users of technology .
Learn more
Related content
relate Experts : Will Loomis, Gary Kessler, and Xavier Bellekens
visualize : Freightliner cargo transport .







